How AI-Generated Personas, Deepfake Tactics and Scripts Are Powering the Next Wave of"Scam-Yourself" Attacks


Cybercriminals continue to refine their methods, and our latest discovery ties together multiple advanced attack techniques into a single campaign which demonstrates the latest trend in “Scam-Yourself” attacks. This particular campaign utilizes fully AI-generated videos created using deepfake principles and AI-generated scripts, created with ChatGPT and hosted on Pasteco and other script sharing websites. In our Q3/2024 Threat Report, we reported a 614% surge from “Scam-Yourself” attacks, those which manipulate people into voluntarily downloading malware or compromising their own security. Shortly after, we announced our Clipboard Protection feature, adding an extra security layer against these attacks. In a matter of days, we uncovered cybercriminals actively leveraging ChatGPT to create and refine malicious payloads. This article sheds light on the latest evolution of these tactics.
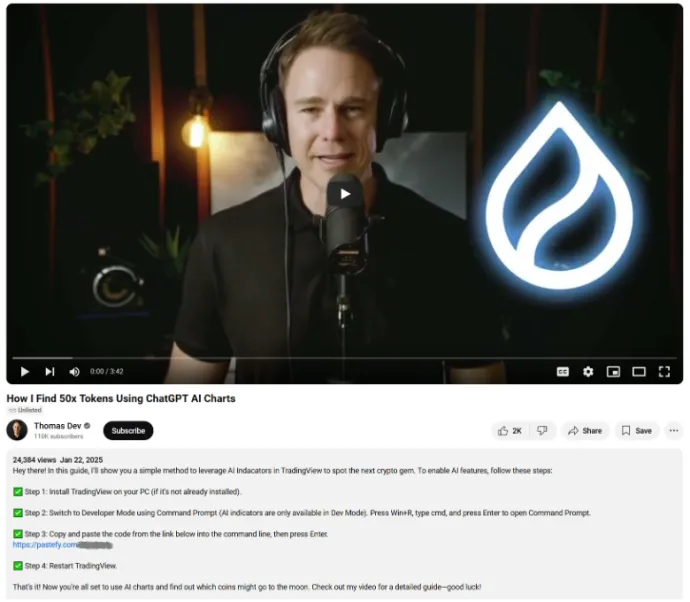
What makes this discovery even more significant is the revelation that the campaign originates from a well-crafted video hosted on a verified YouTube channel with 110,000 subscribers. The channel appears to have been either compromised or acquired, and the video has already amassed +24,000 views. Additionally, numerous YouTube accounts, all variations of the same AI-generated profile, have been used to amplify the scheme, accumulating hundreds of thousands of subscribers.
The Dangerous Convergence of Threats
This campaign connects multiple security challenges:
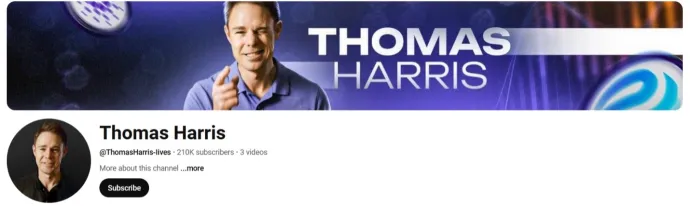
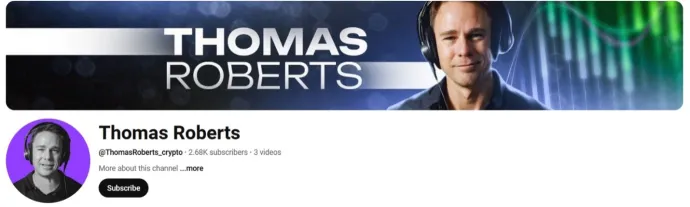
- Compromised accounts: The attack likely started with data theft using information stealers, allowing cybercriminals to take control of a verified YouTube channel and repurpose it for their scam operations. The channel, at first glance, appears legitimate as it includes a list of videos from the official TradingView channel, making it seem trustworthy. However, it also contains an unlisted deepfake video, which can be shared externally. This deception makes it difficult for victims to identify the fraud when viewing the channel. Furthermore, numerous fake accounts have been created, misusing this person as the “face” of multiple fraudulent channels. These fake YouTube accounts using the AI persona of Thomas Harris / Thomas Roberts have hundreds of thousands of subscribers. Many appear to be taken over or bought-off old accounts, some dating back to 2011. These accounts are continuously being taken down. Additionally, the engagement on these channels is manipulated, with all positive comments typically being 'bought' and added in bulk within a short period. Some of the observed fake accounts include @ThomasHarris-Iives, @thomas_hrris_a, @Thomas_View, @Thomas_Harris_Us, @ThomasRoberts_crypto, @tiommewweb3, @Thomas_Now, @RudoAMIN, and @UC6QvVs237am4RyYo1vGHF3g.

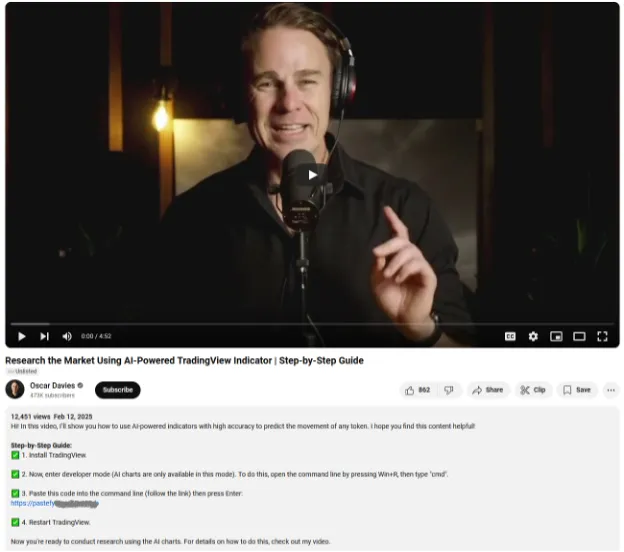
- Deceptive tutorial video: The video presents itself as a tutorial to unlock TradingView’s developer mode, claiming that doing so will provide AI-powered indicators to help users grow their portfolio by a significant percentage. This lure is designed to appeal to individuals looking for an easy way to maximize their financial gains, making them more susceptible to following the video's malicious instructions.
- Deepfake technology: The video appears to depict a completely AI-generated person, with no identifiable real-world counterpart. It utilizes techniques similar to those used in deepfake creation, combining voice, facial synthesis, and body movement replication to create a highly convincing impersonation. Furthermore, we’ve observed more AI-generated videos used across the fake profiles, suggesting attackers are re-creating multiple versions of this well-crafted content.
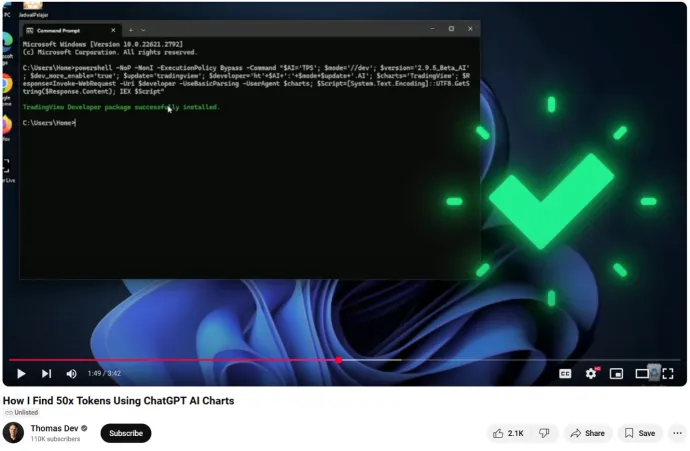
- AI-generated malicious scripts: The script used in the attack was created with AI, in this particular case with ChatGPT. The script itself remains largely unchanged across different variations of the campaign, with the only significant difference being the Command-and-Control (C&C) address. Attackers modify the C&C domain as previous ones are flagged or blocked, demonstrating an adaptive approach to evade detections.
- Scam-Yourself trend: The video demonstrates the same tactics seen in past attacks, instructing users to manually execute harmful commands (e.g., pressing Win+R and entering specific code).
- Hosting services: Attackers have shifted from pasteco[.]com to equivalent sites such as 0bin[.]net or pastefy[.]com, and likely attacker-controlled domains such as pasteco[.]net and pasteco[.]io, a strategy designed in an attempt to evade detection.
- Remote access and data theft: The end goal of this campaign is to install NetSupport or Lumma Stealer, granting attackers full control over the infected system and enabling data exfiltration. Cryptocurrency serves merely as a lure to attract an audience motivated by easy profit.
Malvertising as the origin
Especially when we consider that some of the videos are unlisted and on verified accounts, one might ask how the user comes across such a video in the first place. What we can see is quite a big promotion via Sponsored advertising on YouTube, allowing the videos to pop-up while watching other videos with similar type of content, for example cryptocurrency related investments or other financial opportunities.
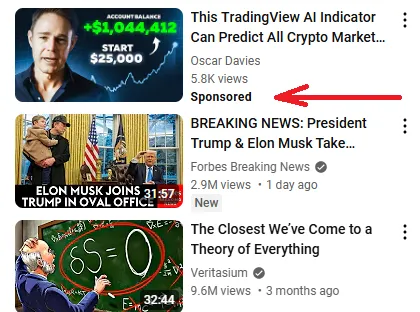
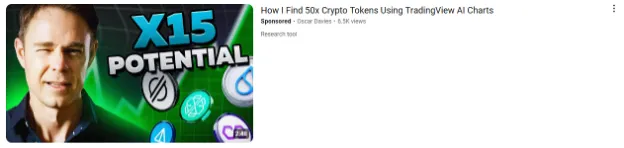
In this case, the account was named Oscar Davies, leading to slightly different variant of the AI generated video. This indicates that the attackers don’t hesitate to re-generate the original video to refresh the content and stay undetected for a longer period of time. When following the advertisement, the video is, in this case, also verified with the checkmark. We can see that the account has nearly half a million subscribers, with the video having 12 thousand views and the time of the analysis. Interestingly, these numbers do not match with the advertised views.
We observed multiple different thumbnails and video titles for the advertised videos, too, likely provided by additional AI driven image generation.
How We Are Protecting Users
Our security solutions detect and block this threat. Our Clipboard Protection feature, designed to prevent clipboard-based scams, is particularly relevant in mitigating such attacks. This campaign reinforces the growing importance of proactive security measures against evolving social engineering threats.
We remain committed to tracking these threats and investigating similar campaigns as they evolve. With deepfakes, AI-generated malware, and social engineering tactics advancing rapidly, proactive security measures are more crucial than ever. Given the involvement of a major player in this space, Lumma Stealer, it is likely that we will see even more campaigns following a similar model. This trend could lead to the creation of even more sophisticated AI-generated personas, making it increasingly difficult to distinguish real from fake. As cybercriminals refine their techniques, vigilance and robust security measures will be essential in combating these evolving threats. Stay safe and always verify sources before executing any online instructions.
Indicators of Compromise (IoCs)
902387e7be025fbe2c4b1a3f2ea212a26f9cbbcf82f656416b362c84089b712b (PowerShell commandline)
a5e0635363bbb5d22d5ffc32d9738665942abdd89d2e6bd1784d6a60ac521797 (PowerShell script)
developer-update[.]dev (C&C)
1b5b3e104f80e09f006a1080fefae16fed2dbf1abb697e464cbef3f2fabc5d90 (PowerShell commandline)
begenokev[.]com/oauth/harum/voluptas (C&C)
2fe60aa1db2cf7a1dc2b3629b4bbc843c703146f212e7495f4dc7745b3c5c59e (Lumma Stealer)
developerbeta[.]dev (C&C)
b89aa5a2837aa09d0caae2bc5be130186f236471411b279049dd1cfce6a5643f (PowerShell commandline)
bcbb6de248a95bfdbf4cfe8db8d84f8a10db2896f27cb90058c69b7bb052d506 (PowerShell script)