How Cybercriminals Are Turning Job Offers Into Malware Traps


Imagine receiving a message on LinkedIn from a recruiter offering an enticing opportunity: a well-paid front-end development project that seems almost too good to be true. It’s a scenario many aspiring programmers dream of, especially those eager to land their first job in the tech industry. However, as this story reveals, the dream can quickly turn into a cybersecurity nightmare.
The Setup
The attack begins innocuously enough. A recruiter reaches out on LinkedIn, pitching an appealing development project with an impressive salary. The target? Entry-level front-end developers, often beginners in the field and eager to seize opportunities. Once the victim expresses interest, the recruiter provides a link to a code repository, ostensibly containing the project files.
In one known case, the recruiter’s high salary offer raised suspicions. This wariness led the targeted individual to scrutinize the repository, revealing malware embedded within the code. The victim wisely decided against proceeding, avoiding infection entirely. Shortly thereafter, the recruiter’s LinkedIn profile disappeared, leaving questions about their next steps unanswered.
A Firsthand Example
This story came to light when we became aware of a similar job offer on LinkedIn. The recruiter claimed to be developing a decentralized application (DApp) for purchasing and claiming ownership of video games using NFTs. The project aimed to provide a seamless cross-platform experience and was allegedly seeking skilled web developers to help with their UI/UX redesign.
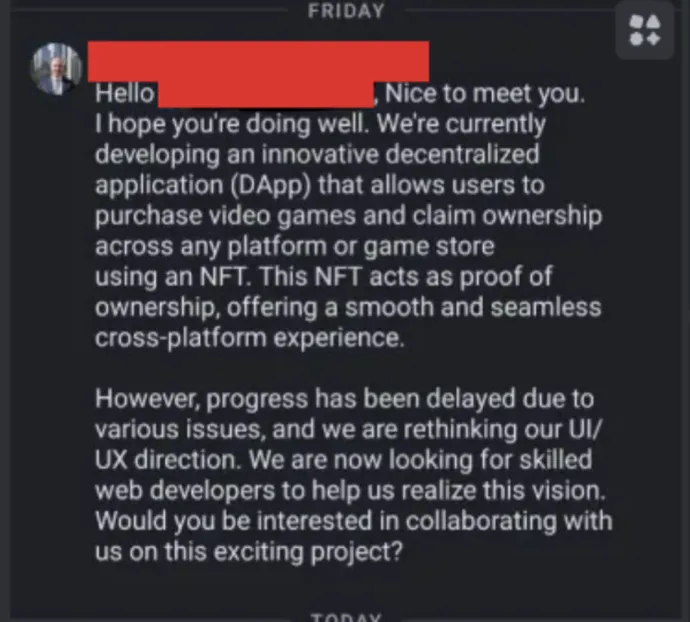
After a few messages, the recruiter shared a Bitbucket repository link. At first glance, the project appeared legitimate, with standard documentation and architecture diagrams detailing the NFT-based system. However, deeper investigation revealed a suspicious obfuscated JavaScript file, onfig-overrides.js, containing malicious code. This file, overlooked by an untrained eye, was designed to:
- Steal login credentials
- Exfiltrate crypto wallet data
- Deploy and execute a Python loader
The recruiter’s polished approach and seemingly genuine project made the scam particularly deceptive.
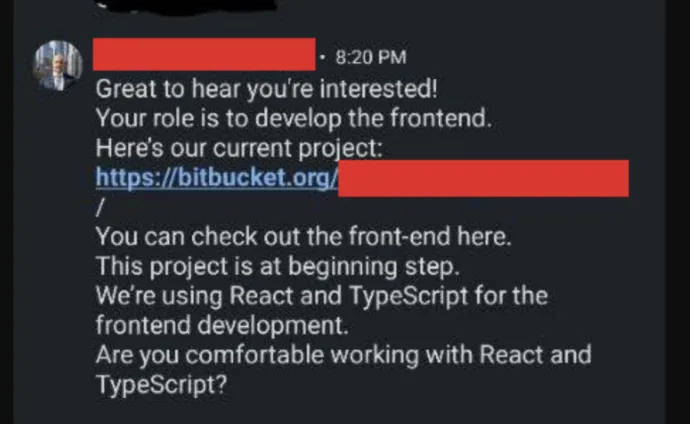
The Mechanism
The attack exploits standard industry practices. In many coding interviews or preparation tasks, candidates are asked to clone a repository, run a local server, and work on the application offline. This is commonplace for front-end developers testing web applications. However, in this case, the repository included concealed malware designed to compromise the developer’s system.
The Step-by-Step Anatomy of the Attack
Once executed, the obfuscated JavaScript file initiated a multi-stage attack process, consisting of two main phases: the initial JavaScript execution and the subsequent Python-based payloads.
Phase 1: JavaScript Execution
- Information Stealing: The initial script acted as an infostealer, targeting:
- Solana wallet configurations and stored crypto wallet data.
- Login credentials stored in web browsers such as Firefox and Chrome.
- Other sensitive information that could be used for further attacks.
- Python Loader Deployment: The JavaScript file downloaded and executed a Python-based loader, which was responsible for delivering the next set of malicious payloads.
Phase 2: Python-Based Payloads
- Remote Access Trojan (RAT): The Python loader executed a RAT with keylogging and advanced spying capabilities, including:
- Remote shell commands: Enabling attackers to execute commands on the victim’s machine.
- Clipboard exfiltration: Capturing and transmitting clipboard data to the attacker.
- Payload downloads: Downloading and executing additional malicious files.
- Browser process termination: Killing Chrome and Brave browser processes to disrupt user activity.
- Sensitive file exfiltration: Searching for and exfiltrating critical files such as .env, readme, and .git.
- XMRig Cryptominer: As part of the second Python stage, the XMRig cryptominer was deployed, exploiting the victim’s computing resources to mine cryptocurrency, which resulted in degraded system performance and increased power consumption.
This structured attack exemplifies the multi-layered and highly intrusive nature of this attack, ilustrating how it moves beyond simple credential theft to fully compromising the victim’s machine.
The Lazarus Group Connection?
Interestingly, the tools used in this attack, named "BeaverTail" and "InvisibleFerret," have been attributed to the notorious Lazarus group in the past. We have strong indications that the attack was orchestrated by the Lazarus group, given their history of sophisticated cyber campaigns and their association with the tools used. The attackers leveraged tools previously linked to high-profile cybercrime, making it critical to approach such situations with caution. While the involvement of Lazarus cannot be confirmed with absolute certainty, the evidence strongly suggests their involvement.
The Broader Implications
While this specific attack focused on credential theft and cryptojacking, the Remote Access Trojan (RAT) also allows attackers to maintain long-term control over infected systems. This could be used for espionage, further malware deployment, or data exfiltration. Additionally, the potential harm could extend far beyond. The perpetrators could use such schemes to:
- Compromise company systems through stolen credentials, allowing further infiltration and unauthorized access.
- Utilize the compromised system for ransomware deployment or additional malware infections.
- Leverage the infected machine as a launching point for future cyberattacks, amplifying the scope of the breach.
The idea of attackers genuinely hiring developers to create malicious tools is not far-fetched, though it seems unlikely in this instance.
Lessons for Job Seekers
This incident serves as a crucial reminder for job seekers, particularly those new to the field, to exercise vigilance when assessing job offers. Here are some tips to protect yourself:
- Have an online interview before proceeding: Before starting any test or downloading files, request a video call with the recruiter to verify their legitimacy and discuss the job offer in detail.
- Verify the recruiter’s credentials: Cross-check their profile and company information. If something seems off, trust your instincts.
- Scrutinize repositories: Before cloning or running any code, scan the files for anomalies. Use reputable security tools to analyze suspicious files.
- Question too-good-to-be-true offers: Unrealistically high salaries or overly eager recruiters can be red flags.
- Use sandbox environments: Run unfamiliar code in isolated environments to prevent potential infections.
- Stay informed: Keep up with the latest cybersecurity threats to recognize warning signs early.
Conclusion
Threat actors are increasingly targeting individuals with highly personalized and sophisticated methods, exploiting both technical vulnerabilities and human psychology. This case serves as a sobering reminder of the lengths cybercriminals will go to exploit human trust and technological processes. For aspiring developers and job seekers, awareness and skepticism are critical defenses. As we face increasingly sophisticated threats, a collective effort to educate and inform will play a crucial role in minimizing risks. By staying vigilant, leveraging security tools, and promoting best practices, we can create a safer digital landscape for everyone—one where opportunities are genuine, and trust is protected.