Beware: Lumma Stealer Spreading via GitHub Comments


As attackers become increasingly innovative, they are beginning to leverage popular platforms more and more to spread their malicious tools. One of the latest and most concerning threats we've observed is the widespread promotion of the Lumma information stealer on GitHub.
What is Lumma Stealer?
Lumma Stealer is one of the top advanced stealers currently in the wild. This sophisticated malware is designed to steal a wide range of sensitive information from victims – stored browser passwords, cookies, cryptocurrency, data from email clients, and more. Lumma is actively researching new attack techniques and is typically one of the first to introduce new methods of credential theft (e.g. the abuse of session cookie recovery for Google accounts).
Often advertised through Telegram and underground forums, Lumma is distributed through a Malware-as-a-Service (MaaS) model, making it accessible to cybercriminals for a subscription fee.
A Growing & Fast Spreading Threat
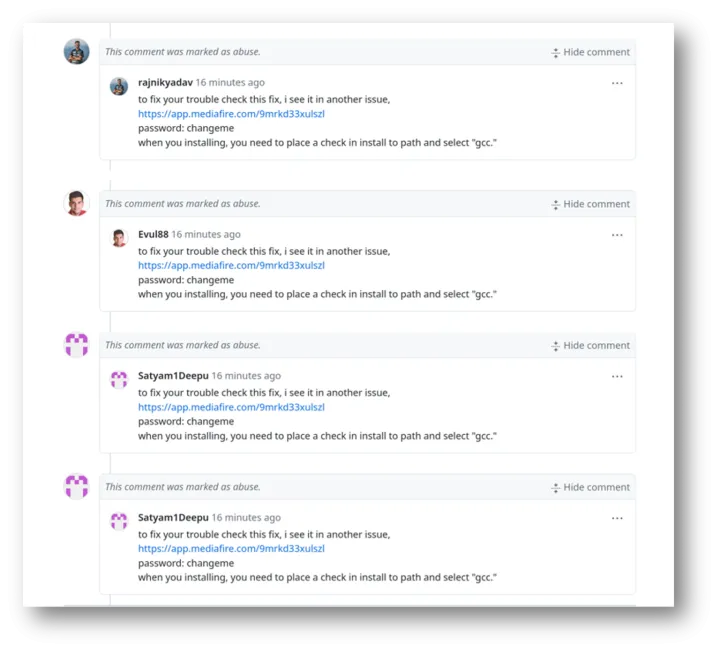
Creators have developed a highly efficient distribution method, utilizing comments on public GitHub repositories to spread the malware. These comments typically include a link to an encrypted archive hosted on mediafire[.]com, along with the password to access the file, often the all-too-common “changeme.” Once the victim downloads and unpacks the archive, their data is at risk of being compromised.
While GitHub is actively working to remove these malicious comments, the sheer volume of posts means that some remain active. Attackers are constantly adding new comments, often faster than they can be taken down. However, we've seen positive progress in the platform's response to this campaign, with an uptick in comment deletions.
Here are some examples of the comments:
A Language Barrier – Telling Signs
One interesting aspect of this campaign is the poor quality of English used in the comments. While this may make the threat easier to spot, it’s worth noting that future attacks could become more polished as cybercriminals begin to leverage generative AI tools to craft more convincing messages. This could make it even harder for users to differentiate between legitimate and malicious content.
Unfortunately, GitHub is not the only platform being exploited in this manner. We’ve also observed similar campaigns on YouTube, where Lumma Stealer and other information stealers are being distributed. In these cases, the attackers might use different passwords and hosting platforms, such as Dropbox, to spread their malware.
These campaigns often target different audiences by masquerading as "Fake Tutorials." They lure users who are searching for software they want but don’t want to pay for by offering instructions on how to "install" the software for free, usually in a form of supposedly cracked version of the software. However, following these instructions leads to the victim unknowingly infecting their device. Similar attack vectors have been observed on other social media platforms, likely from different groups delivering the same malware—or possibly even the same group using this deceptive advertising approach to compromise victims. The tactic remains consistent across platforms.
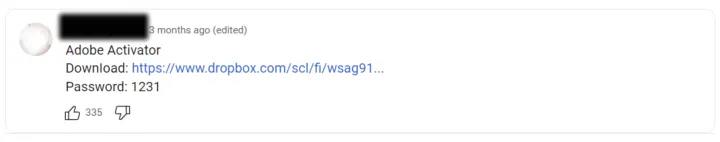
In another campaign we were closely monitoring, an example of a comment on YouTube can be seen below. Similarly inconspicuous to the GitHub campaign, the link leads the user to download an “Adobe Activator” which is in fact once again Lumma Stealer malware.
How to Stay Safe
To stay safe from the GitHub threat, here are a few important steps you can take:
- Use reliable antivirus software: If you’ve accidentally installed the malware, immediately scan your system with up-to-date antivirus software to remove it. We recommend using our Norton software for protection.
- Change your passwords: Update all passwords for accounts accessed on the affected computer and make sure to use strong unique passwords.
- Reset active sessions: Log out of all active sessions on the infected device to prevent unauthorized access to your accounts.
- Enable two-factor authentication (2FA): Wherever possible, activate 2FA to add an extra layer of security to your accounts.
- Keep your antivirus up to date: Ensure your antivirus software is fully updated and all protection shields are enabled. And, do not add unknown software, especially software from untrusted 3rd party sources, to antivirus exceptions.
Comprehensive cybersecurity products, such as those from our family of Cyber Safety brands – Norton, Avast, Avira, AVG and more, are your best defense against these threats.
Sharing Intel on Lurking Threats
As always, we encourage users to remain vigilant when interacting with comments or links on platforms like GitHub and YouTube. If something seems off, trust your instincts and avoid clicking on suspicious links. Together, we can protect your digital freedom and keep your personal data safe.
At Gen, we believe that cybersecurity is a shared responsibility. By sharing intelligence on threats like Lumma Stealer, we empower individuals and organizations to take proactive steps in protecting themselves. Our experts are constantly analyzing the latest threats, and we’re committed to making this information accessible to everyone.
Through collaboration and transparency, we aim to create a safer digital world for all.