Decrypted: Mallox ransomware


Researchers from Avast have discovered a flaw in the cryptographic schema of the Mallox ransomware variant that was prevalent during 2023 and early in 2024. Victims of the ransomware may be able to restore their files for free if they were attacked by this particular Mallox variant. The crypto-flaw was fixed around March 2024, so it is no longer possible to decrypt data encrypted by the later versions of Mallox ransomware.
Overview of the Mallox ransomware
The Mallox ransomware was previously called TargetCompany ransomware, which Avast released a decryptor for in January of 2022. Since then, the cryptographic schema has been evolving – the original cryptographic flaw was fixed by the malicious actors in February 2022, resulting in the decryptor for TargetCompany no longer working. However, as the cryptographic schema kept evolving, the authors made new mistakes which allowed data decryption without having the private ECDH key.
Based on our userbase telemetry, the following picture shows countries with the largest number of blocked attacks of the Mallox ransomware from Oct 2023 to Oct 2024:
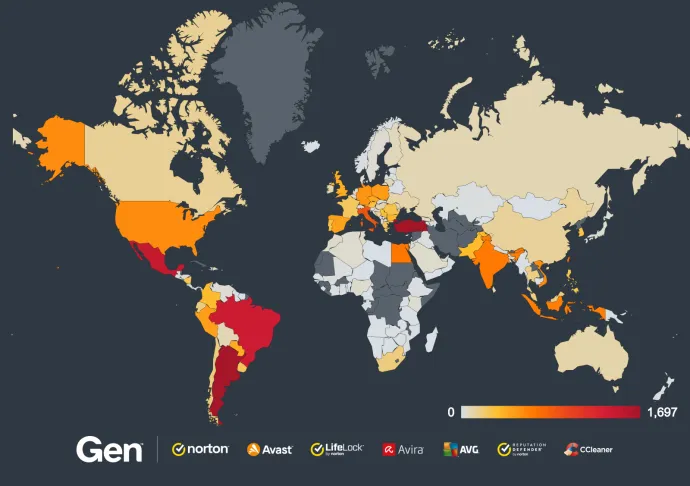
The top 5 countries (based on number of blocked attacks) are:
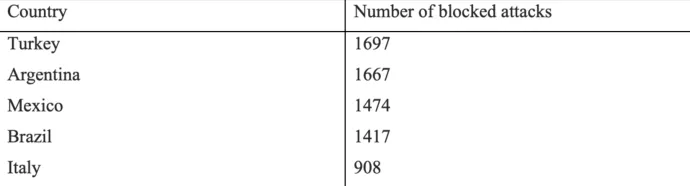
Leak Site
Mallox thread actor also has an account on X, but it has not been maintained since March 2023. Their leak site on the Dark Web shows the list of victims up to June 2024.
How to recognize the decryptable version of Mallox?
The decryptable versions of Mallox were spreading from January of 2023 to about February 2024 (based on the compile time of the samples). Decryptable files can be recognized by the following extensions:
- .bitenc
- .ma1x0
- .mallab
- .malox, .mallox, .mallox, .malloxx
- .xollam
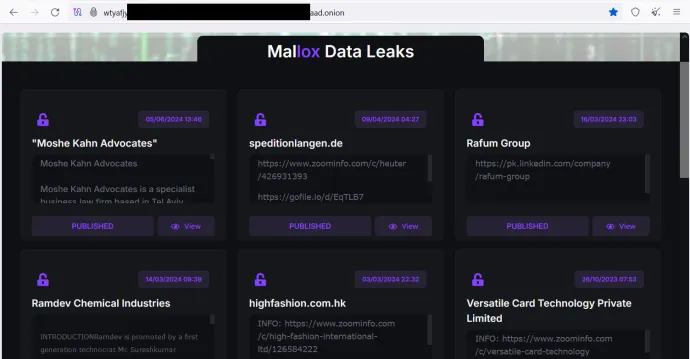
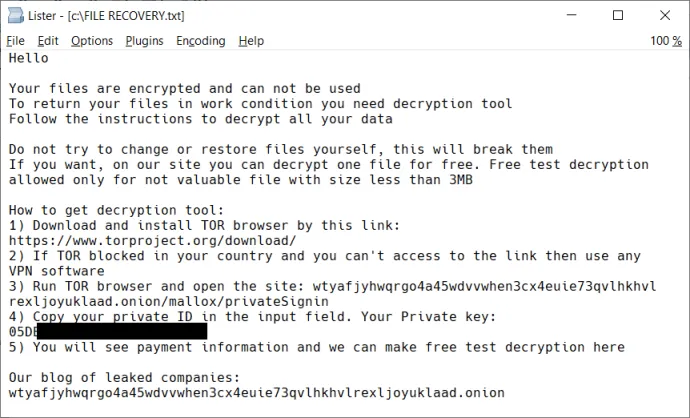
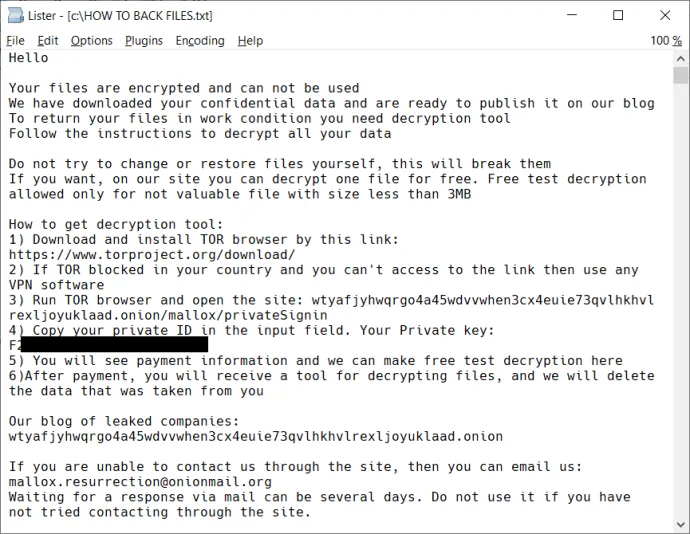
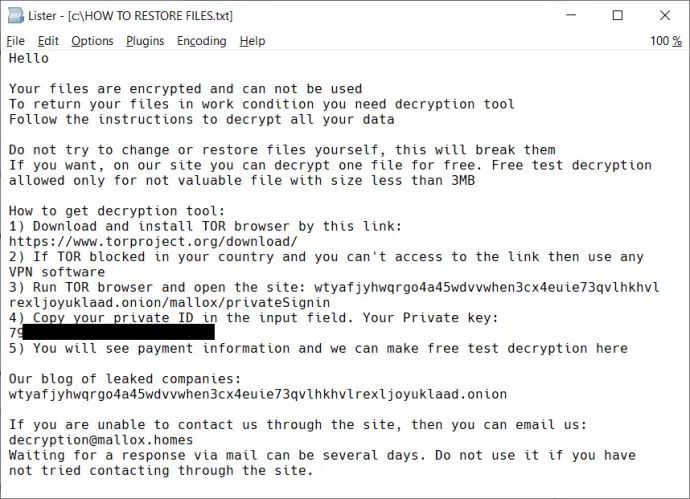
During file encryption, Mallox ransomware leaves a ransom note in each folder. The possible file names are:
- FILE RECOVERY.txt
- HOW TO BACK FILES.txt
- HOW TO RESTORE FILES.txt
The following pictures show the ransom note content:
How to use the Mallox ransomware decryptor
Download the decryptor here. If you still use 32-bit Windows, you can also get the 32-bit version of decryptor.
Run the decryptor, preferably as an administrator. It starts as a wizard, leading you through the configuration of the decryption process. The decryptor must be executed on the same computer where the files were encrypted.
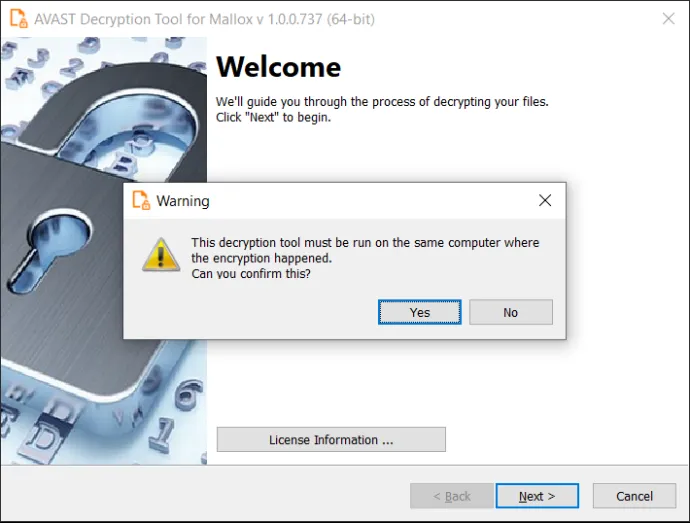
On the next page, the user is asked to provide a list of locations (drives, folders, files) that are to be decrypted. By default, the decryptor provides a list of all local disk drives.
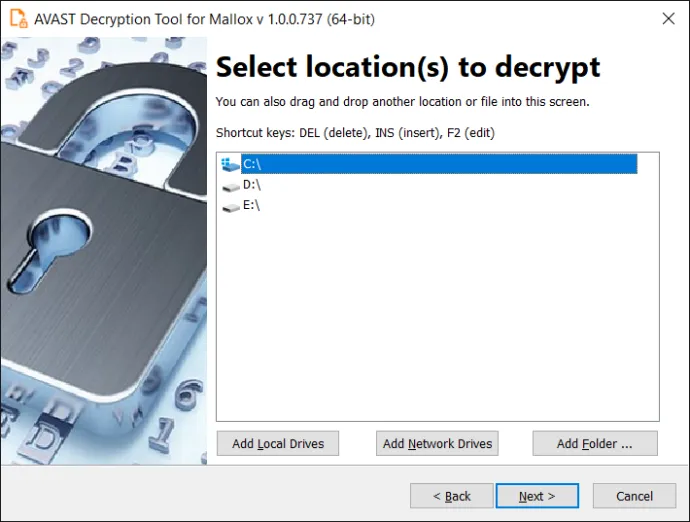
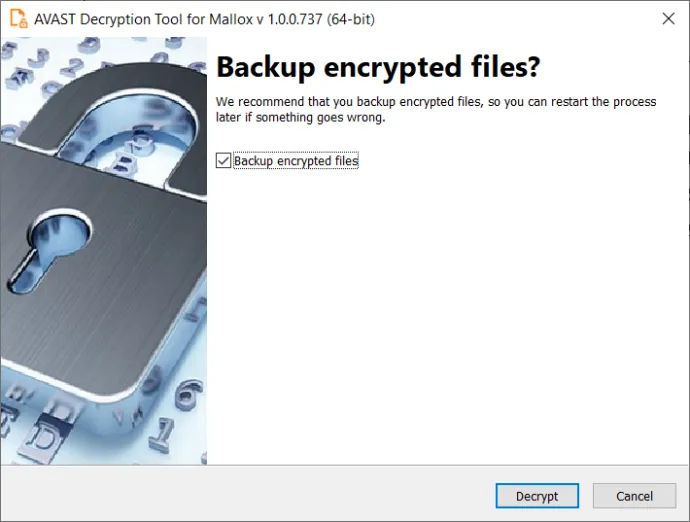
On the final page, you can opt-in to back up your encrypted files. These backups may help if anything goes wrong during the decryption process. This option is selected by default, which we recommend. After clicking Decrypt, the decryption process begins. Let the decryptor work and wait until it finishes decrypting all of your files.
Indicators of Compromise (IOCs)
The list of Mallox samples and extensions of encrypted files follow:
a340ef5adb00a2bf1a0735600491ca98ac8045b57db892dedc27575a53b25056
- .bitenc
003ea0712cd31a75f5dfb6a23d2d12ea1e615f7601574ade09b6b61e3b7ed2b0
25719f4afa357af8141e42fa9a0499c08fd94011690b8e75e8a22ce6af31c825
311d3c07ceabb08fd3f2486ad99fb6a7b2ea881135ef3f75840f9fd859fec537
34c04dff26da88c339eeb1220f7e8ac8cfc47a340237c37edbae96c8fd1ee5e5
6976ffaa2deac082dedcd30e2ecb2faa86e5361d1c22d6678baf44985ef217ce
8bc92f4a5b1429397be96fe264a543752e92d73a4e7ed9fbdbb21e654c2cb838
a2b63fae8c83a02f57fff4d932a1e846765a70b18bfae65c127f72010674cce8
b87712413054cffeb98212babcea85c8f6f460e28269717c31e2e84bd4192d02
dd871fe134be4b972c6e22efbb6c7d59d908127c3148ef1958c43ba5a33185ed
- .ma1x0
0653d7a8a2267e6e7db5c8f39afca7f358ce097d7c0724c0c70493f6cf30f43d
0706c9d8413a6ffb7dc68d6a69a9ced942ad2e9f3318a2cf2e535d44661b52a2
1da63eb16aa6d7ec9e6d46f3897275bb238ac8156fcee3552bb3b41af73fee44
311eac772bea66edba4c9f180d55776f0e8c40c64d6066de354ae68504f69a77
3742b60308d2a7fb47c69a625dfdaae16561db5ee7353ce9a8a02110961192f5
374a979d2b8b45d23e3310676256624ab96bd604c2eb11f327c3e5044a95654a
3f044ba34bdf3c049e1f2468c91339ffc71d61fea913a43f876b8ba05211d0dc
3fc75983ed3c5ac1879d862760523e2986907fc9a177c9b740b5b36e6e28f9d9
4674370e64733f2f634251da6967fe96f02ac4654543b36b1b80e765495bfe4e
5133aab38acbe99380dccf5f69150c887467a910cc3052b5054ffca56e149847
(and 30 more)
- .mallab
03596723ecb5be777b1e3ec5deb414dc78155a30a466b2b25a4574f4db9a568a
0e37d23af67569980f74ee9fd76ffc03280ea79ea581cc00c8c5030049739e29
116bcf7ff3927139f92fcafad0ee8105e90c6e11f57e913976d65b1d326874f6
197e192e8c3a7df7a4e00a7c67d91bbf1cff1dbe756ec6e5e446f9a16df96ad8
1bc30c4abebb326a548401b665540b5203591599220889907f316f5ebdf99dd5
1c615da28dac08f6434eb7737f6102484cef6c90564a6562320e1dc3fe48e584
1c8b6d5b79d7d909b7ee22cccf8f71c1bd8182eedfb9960c94776620e4543d13
1d217728faecddc1699af6761a9dfb22fe0ed648abc47639017c3eac7cfa0f85
1db038fea314da6884990e1ecdd5579ade64803db4d29384c9ac752cf44a354c
1e7342641f88f9df8b7830544821531544585f30bea7fd895b7db8a0a461896b
(and 74 more)
- .mallox
0064cafe8474c7a29e514d16825cb2a2b804e64c3f0d7f660b3b3e76cb37d7cc
1cf818229b7d06a4caf2c6bd4b3b3e8b2cc865ba7b77b7176f412ccb08e3f6d8
55d568e14868cc4a2583db29688996bc43f8f27bfb8b3ddb95662f7f9deac4b4
5abe151418fc18090eba2c62ffdefe738250151f34ea1b290f63df702f68deac
7105930cb8859795303ebd254ad785faf13d6dacd41fda733a29f40e2c551fc6
90672eb92326724cc125c276faa3c8bba7b837d0b9b13977c4c67330d7cfddae
ce198296ebb3def9b1c929b3e54072e831e05d993eda48129987ef93d717a7d6
df29d5c4a750663440ce76d6804ce88e03faeef9591ec0b3b9ca348a6c930b7f
2044bc33cf855b4add30312da75ac8daa408197408da88ecd520d90bdef550ff
3cd0e666eef8439064a78aa8d60669c9ec98edea60ec0894548bad6c97954970
(and 8 more)
- .malloxx
0427a9f68d2385f7d5ba9e9c8e5c7f1b6e829868ef0a8bc89b2f6dae2f2020c4
0463277782f9e98b0e7a028cea0f689a81cf080fa0d64d4de8ef4803bb1bf03a
19570b184cacd8288a3d0756eeff7568af9970afc2d63dce69101d5ece88dfb6
21f33c588bba58522d5e475f43012a886d42be956c644cc000e87c59c4cf9008
2b4ec26fc1c25f56e5469f3550815cf6e488eab6641fbf661464ec7170a66d93
2fd3c8fab2cfaaabf53d6c50e515dd5d1ef6eceeebdd5509c23030c4d54cb014
36079d6856ba2935e17401f80caa160195460e0afefc191b0fe04c31d2f9f4b6
3ab42c1bd05fabaf3276a66f0a9f7d8a509aec4835b321d03b3165a71dd5924d
66038da15ef19678b4a98531b045e3e7e924a8f1e508732054648fac77a5fd9f
75498c3fa25bbbcdaa970d83376c4b8f6e5403980141125e9b05a389584cca8b
(and 26 more)
- .malox
86ec7e79b5eb6f22fc657203b8bc0da895f09045d3252030130eff0830018466
bfcf5d57790f28dd78d5f351776e0fee4efd537e9490c3105d5c6bbf37e8b241
- .maloxx
0598708adf2aabe3aa81919f50dc0fd65acf4d4ed80ad32dc43d09a3bab7b50a
10f96f64659415e46c3f2f823bdb855aab42d0bfced811c9a3b72aea5f22d880
258101f7b1767837217a242fee4e71896df06d758e97fe79d996224d67f7d136
4ed74a205fad15c843174d7d8b30ae60a181e79f31cc30ebc683072f187e4cdd
52e281f8cde1fd07b54aecbac93cc97890a3c59ff8bac5627b5dfbd7c07a4e48
7f81d7b71fff4ab3abc82e1ccf83bf386bb1172b0978238ae3ff9ea912c4e7e3
9acbc6b9342e22059c02db89c629d56b2ada8b56abe94f2a901ed1252beac2cd
- .xollam