Gen Q2/2024 Threat Report


Foreword
The Q2/2024 Gen Threat Report is here, marking the launch of our new series under the unified Gen brand, replacing the Avast Threat Report series. As we continue integrating threat telemetry across our diverse cyber-safety solutions—including Avast, Norton, AVG, Avira, and LifeLock—we're gaining an even more comprehensive view of the evolving threat landscape, which we look forward to sharing with you in this series.
This quarter—April through June 2024—continued to highlight the relentless nature of cyber threats, with a staggering 46% increase in attacks year-over-year. Although we observed a slight dip compared to the previous quarter, the overall threat landscape remains highly active, with over a billion unique attacks being blocked by us each month. Scams and malvertising continue to dominate, making up more than 87% of threats on Desktop and 93% on Mobile. Notably, attacks utilizing AI-generated techniques, such as scams via phone calls or deepfake videos, are becoming increasingly common, further complicating the threat environment. Browsers and the Web serve as the primary attack surface, accounting for 95% of all threats.
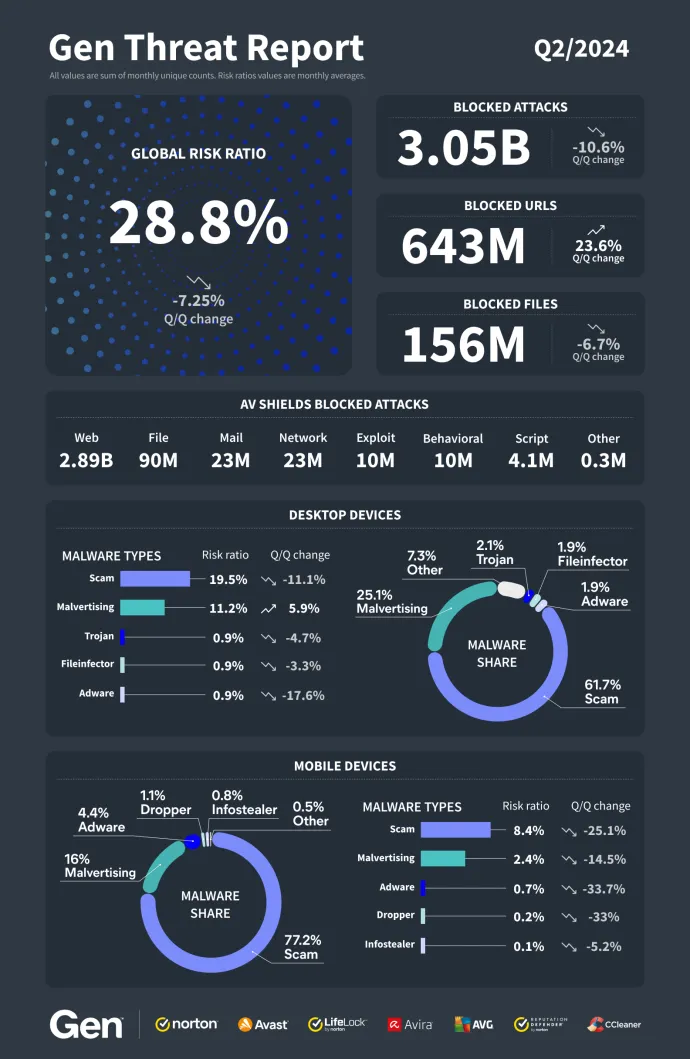
Scams remain a dominant threat this quarter, with new techniques emerging and old ones being repurposed, often with alarming sophistication. Financial scams, particularly investment scams, have surged as threat actors increasingly leverage AI-generated deepfake videos on YouTube, featuring high-profile events and celebrities to attract victims. A standout example is the CryptoCore scam, where attackers used compromised YouTube accounts and deepfake videos to steal at least $5 million globally in recent months. They lured victims into fake cryptocurrency giveaways with highly convincing content. Fortunately, we successfully blocked a significant portion of their attacks, preventing further losses. However, the sophistication of these scams underscores the growing risks to users, as attackers continue to exploit trending topics and advanced technology to enhance the reach and impact of their fraudulent schemes.
Another concerning development is the rise of part-time job scams (also known as task scams). These have evolved from text-based interactions on Telegram to more sophisticated AI-generated voice communications, adding a new layer of deception and realism. Additionally, dating scams remain prevalent, particularly in Europe, while technical support scams (TSS) and fake invoice scams continue to target users in Japan, the US, and Australia. The emergence of ClearFake type of attack, where attackers convince users to run malicious scripts under the guise of fixing common Windows issues, further illustrates the growing ingenuity of scam tactics. This quarter also saw significant activity related to EchoSpoofing—a major attack that exploited email routing misconfigurations of a security solution to deliver millions of malicious emails.
A worrying trend this quarter is the return of fake antivirus scan scams—a tactic many believed was a thing of the past. These scams trick users into thinking their devices are infected and are now more convincing than ever. You can read more about it in the featured story of this report.
Stolen user data and personal information – the pieces used to take over identities – continues to be digital gold for threat actors. In this quarter, we’ve seen a spike in activity from various identity theft-related threats, such as information stealers like AgentTesla, which remains widespread on desktops. On mobile, banking trojans like TeaBot, SoumniBot, RewardSteal, and Medusa are growing rapidly. These threats are slipping through onto the PlayStore and posing a serious risk to users.
On a more positive note, law enforcement made significant strides this quarter. Operation Endgame, led by Europol, disrupted major botnet providers such as IcedID, SmokeLoader, and Trickbot resulting in several arrests and notable setbacks for malicious operations. Furthermore, the U.S. Department of Justice also played a crucial role in dismantling the notorious 911 S5 botnet, while actions against the DDoSia botnet led to multiple arrests. Additionally, efforts to combat Remote Access Trojans (RATs) have shown positive results, with operations targeting threats like Hive. It will be interesting to see how the botnet landscape evolves following these high-profile arrests. Will a new kingpin emerge to replace those who have been taken down?
Despite these successes, some botnets, such as Twizt, have adapted by spreading ransomware strains like LockBit Black through email attachments. This quarter saw a notable 24% increase in blocked ransomware attacks in our telemetry, with particularly sharp spikes in the US, UK, and India. Nevertheless, there have been significant victories in disrupting ransomware operations. We’ve continued our commitment to aiding victims by providing free decryption tools, including our latest release for the DoNex ransomware.
Lastly, Advanced Persistent Threat (APT) groups, particularly those linked to North Korea like Lazarus and Kimsuky, remain active, with several campaigns targeting Asia, including the GuptiMiner campaign. On mobile, we’ve seen adware sneaking into the PlayStore, designed to generate fraudulent advertising revenue through background clicks.
And as we delve into these insights, we invite you to explore the full breadth of information contained in this report. With a comprehensive view of the current threat landscape, we hope this new Gen series offers even more value and clarity than its predecessor. Stay safe, avoid blue screen incidents, and enjoy diving into the report.
Jakub Křoustek, Malware Research Director
Methodology
This report is structured into three main sections: Desktop-related threats, where we describe our intelligence around attacks targeting the Windows, Linux, and Mac operating systems, with a specific emphasis on web-related threats, and Mobile-related threats, where we describe the attacks focusing on Android and iOS operating systems.
We use the term “risk ratio” in this report to denote the severity of specific threats. It is calculated as a monthly average of “Number of attacked users / Number of active users in a given country.” Unless stated otherwise, calculated risks are only available for countries with more than 10,000 active users per month.
A blocked attack is defined as a unique combination of the protected user and a blocked threat identifier within the specified time frame.
Moving forward, our quarterly threat reports will be informing about the threat landscape situation as seen from the suite of Gen cybersecurity brands. We continuously enhance our threat telemetry and anticipate further refinements in our future reports.
Featured Story: Fake Scan Scams - A New Twist on an Old Trick
For veteran internet users, the mention of fake antivirus scams might evoke memories of the early 2000s, when cybercriminals exploited fears of malware infections with alarming effectiveness. Back then, cybercriminals tricked users into thinking their computers were infected, showing fake antivirus interfaces detecting nonexistent threats. In a panic, users purchased licenses for these fake programs, which only simulated antivirus functionality without real protection. Some even uninstalled their real antivirus software, believing the fake one was superior. These fake antivirus scams were a goldmine for cybercriminals, generating hundreds of millions in illicit profits.
Fast forward to today, and we're seeing a new twist on this old trick. This time, the scammers have upped their game, making their schemes more sophisticated and harder to spot. Whether you're a seasoned user or new to these tactics, it’s crucial to understand how these scams work and how to avoid falling victim.
The Evolution of Fake Antivirus Scams
Back in 2008 and 2009, cybercriminals used fake antivirus (Fake AV) software to scare users into buying bogus programs. These fake programs, often referred to as scareware, would bombard users with alarming, fake virus alerts, prompting them to purchase the fake software. The scale of these scams was immense, with countless victims and hundreds of millions of dollars lost. Reports from that time highlight the scale of the problem, with numerous victims falling prey to these tactics and the total financial losses running into millions of dollars.
Today, cybercriminals are rehashing this old scam, capitalizing on the public discussion about cybersecurity following numerous data breaches and cyber incidents in previous months. The criminals have now refined the fake antivirus scam with two significant changes:
- Promoting Real Antivirus Software: Instead of pushing fake software, these scams now promote well known antivirus brands like Avira, AVG, Avast, Norton, McAfee, Kaspersky and others. The renewal process occurs on the actual antivirus company’s website, adding a layer of credibility.
- Abusing the Windows Notification System: Scammers exploit the Windows notification system to make their alerts look like genuine system warnings. This tactic makes the scam much more convincing, pushing users to act quickly.
How the Fake Scan Scam Works
Cybercriminals use aggressive pop-up alerts that mimic the look of real antivirus programs appearing in your browser. These alerts often claim that your computer is infected with multiple viruses, urging immediate action. These messages can mimic the style of legitimate antivirus programs, prompting users to click on links that ultimately lead to real antivirus sites. They then direct you to purchase a real antivirus product, earning commissions through the referral programs of these legitimate companies.
To add to the deception, these fake alerts abuse the Windows notification system. By sending alerts that appear as system messages, scammers add an extra layer of credibility, making it more likely that users will fall for the ruse. This tactic plays on the trust users have in their operating system, making the scam seem all the more real and urgent. If the victim closes the browser alerts will keep showing up in Windows, even if the computer is locked.
Delivery Mechanisms: While push notifications from the browser are a common delivery method, the attack often starts with a fraudulent email. Users receive a phishing email from what looks like a legitimate antivirus brand with a link that, when clicked, initiates the Fake Scan scam process.
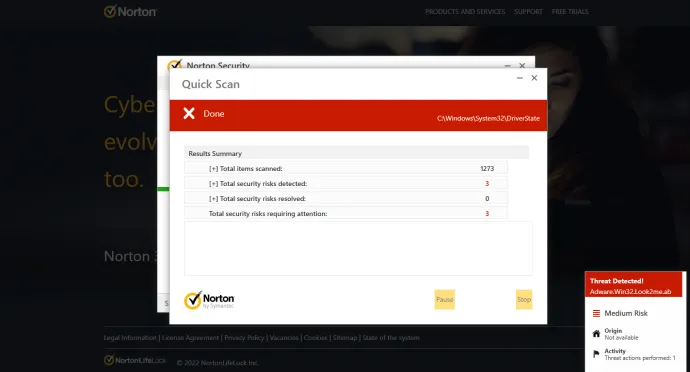
The following are the Fake AV Scan scam steps:
- Browser Pop-ups: The scam begins with pop-ups appearing in your web browser, claiming that your system is infected. These alerts can appear even after you close your browser, continuing to show up on your desktop and lock screen.
- Varied Messages: Beyond infection warnings, scammers also use messages like "Your Google account has been hacked" to instill fear and urgency.
- Fake Scanning Interface: Clicking on these alerts takes you to an interface resembling a legitimate antivirus scan, which shows multiple fake threats.
- Purchase Prompt: To "remove" these threats, the interface prompts you to buy or renew a license. When you click to proceed, you are redirected to the actual antivirus company’s website to complete the purchase.
- Referral Links: The URLs involved often include referral codes, showing that the scammers earn commissions through affiliate programs.
By promoting legitimate antivirus products, cybercriminals can exploit affiliate programs to earn commissions on each sale. This not only dupes the user into buying unnecessary software but also diverts revenue to the scammers at the expense of both consumers and legitimate antivirus companies.
Protecting Yourself from Fake Scan Scams
To help safeguard against these sophisticated scams, follow these essential tips:
- Stay Vigilant: Be cautious of any antivirus alerts that appear while browsing. Fake Scan scams often replicate the look of legitimate programs, making them hard to distinguish.
- Verify Warnings: Always check antivirus alerts through your installed antivirus software, whether that’s locally on your device or by logging into your account in the browser.
- Manage Notifications: Avoid granting permission to install push notifications from untrusted websites. Only allow notifications from reputable sources to minimize the risk of malicious alerts.
The Scale of the Problem
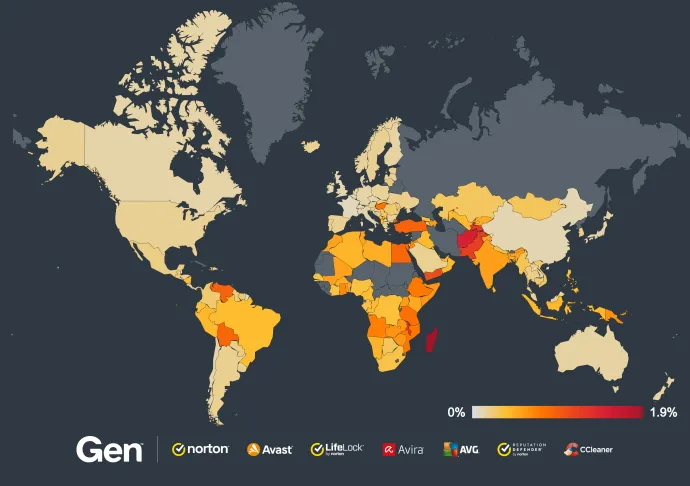
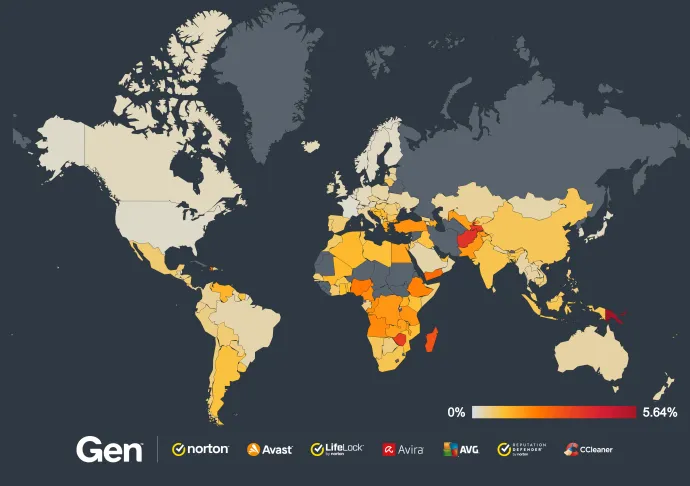
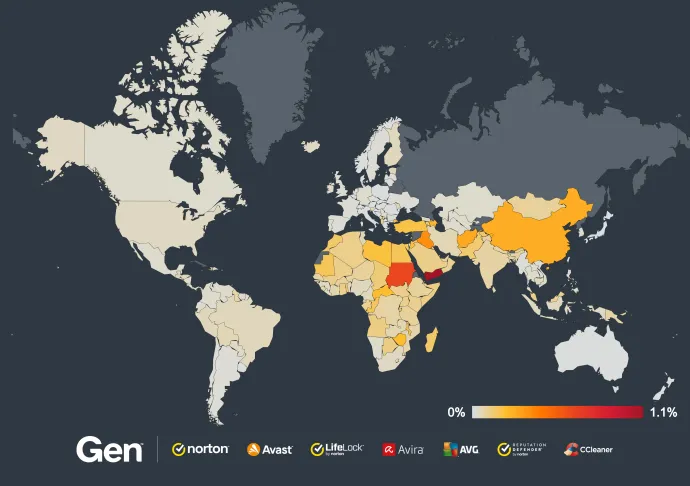
So how big of a problem are fake antivirus scams? During this quarter alone, we have protected over 1 million users from these attacks. While the attacks are occurring worldwide, they are particularly active in North America, South America and Europe, with significant incidents also reported in countries like India or Japan.
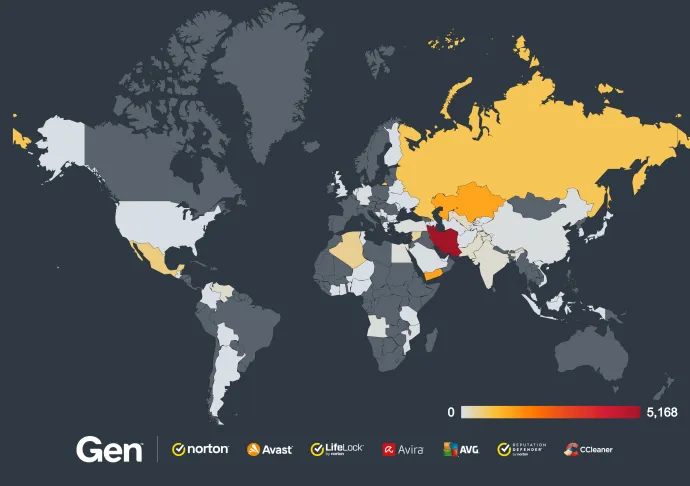
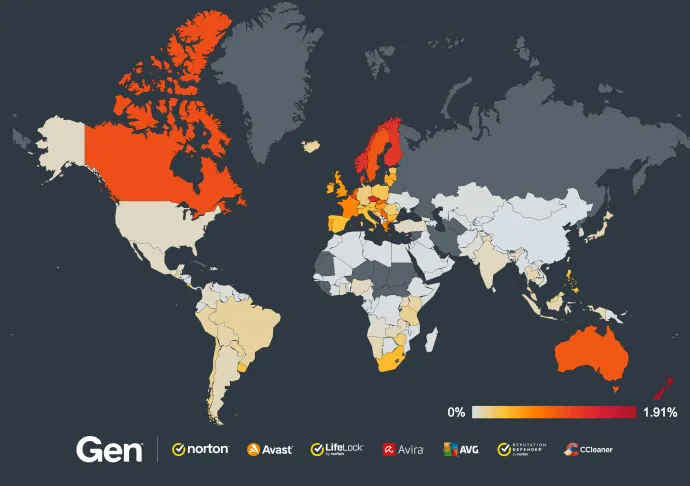
To give you a clearer picture, here's a heat map showing the Fake Scan attacks blocked in Q2/2024 worldwide:
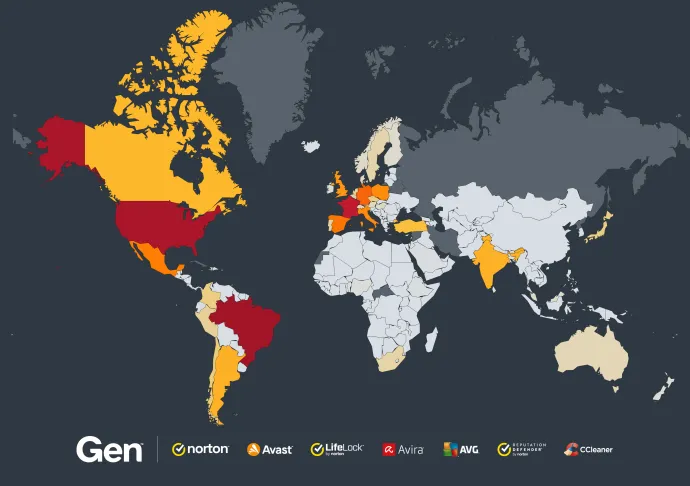
These are the top 10 countries with the most Fake Scan attacks blocked:
- Brazil
- United States
- France
- Germany
- Spain
- Mexico
- Italy
- Poland
- United Kingdom
- Argentina
The sheer volume of these attacks highlights the global scale of the problem. Cybercriminals are leveraging sophisticated tactics to target users everywhere, exploiting their fear and urgency to drive these scams. The widespread nature of these attacks, coupled with their high success rate, underscores the importance of people around the world understanding the potential threat of these scams.
Conclusion
The old fake antivirus scams, where cybercriminals made millions, demonstrated the effectiveness of exploiting fear and urgency. Now, with the added layer of legitimacy provided by the illegitimate promotion of real antivirus products and the Windows notification system, these scams are more convincing than ever. It is essential to remain vigilant, verify the authenticity of alerts, and only trust reputable sources to ensure you don't fall victim to these evolving threats.
David Jursa, Malware Researcher
Luis Corrons, Security Evangelist
Desktop-Related Threats
Advanced Persistent Threats (APTs): Asia's Cyberfront
An Advanced Persistent Threat (APT) is a type of cyberattack that is conducted by highly skilled and determined hackers who have the resources and expertise to penetrate a target's network and maintain a long-term presence undetected.
Asia continues to be a hotbed for Advanced Persistent Threat (APT) activity, with various actors actively targeting countries such as South Korea, Myanmar, Vietnam, the Philippines, and Cambodia.
This wave of cyberattacks highlights the growing amount of geopolitical tension and cyber espionage in Asian countries. Among the many actors involved, Mustang Panda stands out as one of the most persistent groups. Identified in operations across Mongolia, Vietnam, and Myanmar, Mustang Panda has become infamous for their heavily used sideloading techniques to deploy malicious payloads. These payloads often involve the Korplug malware, a tool primarily used to steal sensitive documents from compromised systems, illustrating the group's focus on intelligence gathering and long-term infiltration.
The Sidewinder group poses yet another significant threat in the region. Traditionally associated with operations targeting Pakistan, Sidewinder has recently expanded to target countries like Sri Lanka and the Maldives. This expansion highlights the group's evolving tactics and its ability to adapt to shifting geopolitical dynamics. Sidewinder’s campaigns are notable for their ability to exploit vulnerabilities in diverse environments, demonstrating a sophisticated understanding of both technical and geopolitical landscapes.
In addition to Mustang Panda and Sidewinder, the region has also seen activity from other advanced threat actors. For instance, a relatively new group has launched widespread attacks across Thailand, Vietnam, Saudi Arabia, the Philippines, and Taiwan. What sets this group apart is its use of custom malware, including advanced shellcode capable of manipulating and bypassing the security measures of well-known security vendors. Fortunately, the specific vulnerability exploited by this group was quickly reported to the vendor and has since been patched.
In Q2/2024, the Lazarus group, a well-known North Korean APT, began particularly targeting freelance developers working on NFT and crypto-wallet projects. Lazarus has demonstrated a keen interest in the cryptocurrency market, leveraging legitimate platforms such as "freelancer.com" to distribute malicious JavaScript to unsuspecting developers. The group has also employed GitHub repositories to spread their malicious NPM-based packages. These packages, once installed on Windows, Linux, or macOS systems, begin by gathering basic system information. They then scan the victim's web browser for cryptocurrency wallet extensions, such as those from Binance and Coinbase, before deploying a custom Python backdoor.
This backdoor is designed for a range of malicious activities, including fingerprinting, remote control, keylogging, data exfiltration, browser credential theft, and even the downloading of remote access tools like AnyDesk. The sophistication and focus of Lazarus on the cryptocurrency sector suggest a calculated effort to exploit this growing market for financial gain.
To add to the complexity of the Asian threat landscape in Q2/2024 we reported on GuptiMiner, a highly sophisticated threat with a unique infection chain. The threat actors behind GuptiMiner employed a range of advanced techniques, including DNS requests to attacker-controlled servers, sideloading, extracting payloads from seemingly innocent images, and signing their payloads with a custom trusted root anchor certification authority.
The criminals running GuptiMiner have been capitalizing on an insecurity within an update mechanism of an Indian antivirus vendor to distribute the malware by performing a man-in-the-middle attack. Based on similarities between the GuptiMiner operation and the Kimsuky keylogger, we believe the campaign was orchestrated by notorious North Korean APT group Kimsuky.
The main objective of GuptiMiner is to distribute backdoors within big corporate networks. We’ve encountered two different variants of these backdoors: the first is an enhanced build of PuTTY Link, providing SMB scanning of the local network and enabling lateral movement over the network to potentially vulnerable Windows 7 and Windows Server 2008 systems on the network. The second backdoor is multi-modular, accepting commands from the attacker to install more modules as well as focusing on scanning for stored private keys and cryptowallets on the local system.
Interestingly, GuptiMiner also distributes XMRig on the infected devices, which is a bit unexpected for such a thought-through operation.
Luigino Camastra, Malware Researcher
Igor Morgenstern, Malware Researcher
Jan Rubin, Malware Researcher
Bots: Spring Cleanup
Bots are threats mainly interested in securing long-term access to devices with the aim of utilizing their resources, be it remote control, spam distribution, or denial-of-service (DoS) attacks.
The Windows botnet landscape was a wild one in Q2/2024. At the end of May, an operation dubbed Operation Endgame, coordinated by Europol, targeted various droppers and bots such as IcedID, SystemBC, Pikabot, SmokeLoader, Bumblebee, and Trickbot. The operation focused on arrests, sever takedowns, domain seizures and physical searches to disrupt popular providers many other threat actors rely on to deploy their payloads. At similar time, U.S. DOJ-led operation disrupted the 911 S5 botnet. According to the court documents, the botnet spread through various VPN programs (such as MaskVPN and DewVPN) and pay-per-install software bundles. The main aim of the botnet was to provide residential proxy to other threat actors to allow them to mask their operations.
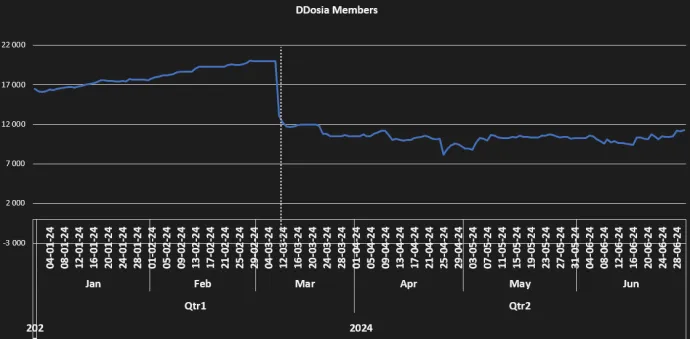
DDoSia came rather late to the spring cleanup - Spanish Civil Guard paid a visit to three DDoSia participants recently which resulted in arrests and hardware confiscation. Arrests aside, DDoSia project seems to have hit a plateau. The cadence of new messages on their channel is more-or-less stable as is the number of participants in the project. As usual, the most frequent targets were banks. This season also brought tax period in many countries, including Ukraine, prompting the group to target various online tax return platforms. Frequently, we saw attacks on websites of various European cities such as Berlin or Krakow; nevertheless, the impact of such attacks is debatable. Interestingly in June, we saw rapid changes in C&C infrastructure again which would point to issues with their infrastructure, especially since these outages impact their activity.
Unfortunately, Twizt did not participate in this spring cleanup. It has shifted its focus from a sextortion campaign to malicious spam campaign loaded with LockBit3-based ransomware, dubbed LockBit Black, in its attachment.
As a whole, we’ve seen an overall decline in bot-related threats, with many notorious strains having two-digit drops in their perceived prevalence (Emotet -50%, Tofsee -22%, Twizt/Phorpiex -17%, Amadey -36%, IcedID -18%). We presume that this trend may continue in the next quarter due to the takedowns which might affect their operation.
In terms of Linux bots, the quarter started with the Goldoon botnet exploiting CVE-2015-2051 and targeting D-Link devices. The usual plague of Mirai/Gafgyt/Xordos bots has a new companion this quarter - V3rs3Bot. Unfortunately, augmenting bots with kernel rootkits continues, leading to many yet-undetected bots in the wild. For instance, we found a malicious kernel module that misleadingly uses “Netfilter core team” as an author that also contains backdoor inspired by its reverse shell.
Adolf Streda, Malware Researcher
David Alvarez, Malware Analyst
Coinminers: Decrease Globally but Are Not Dead
Coinminers are programs that use a device's hardware resources to verify cryptocurrency transactions and earn cryptocurrency as compensation. However, in the world of malware, coinminers silently hijack a victim's computer resources to generate cryptocurrency for an attacker. Regardless of whether a coinminer is legitimate or malware, it's important to follow our guidelines.
Despite a continuing decline in the prevalence of coinminer malware in Q2/2024, coinminers are still leveraged by threat actors. In our recent report on GuptiMiner, we described that one of the stages on devices compromised by this threat was an XMRig coinminer. Although distributing a coinminer is a bit unexpected for such a thought-through campaign, it proves that threat actors still want to make a coin when they see an opportunity.
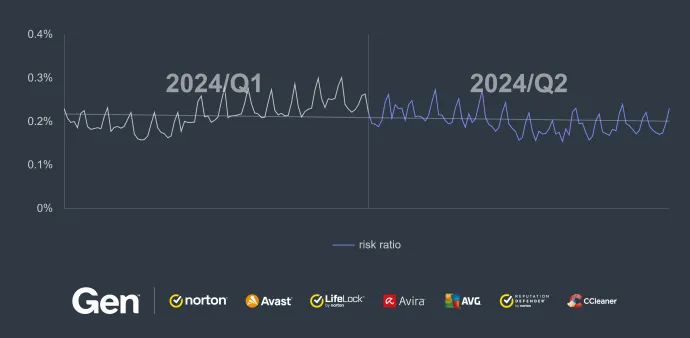
Overall, the risk ratio dropped by an additional 18% in Q2/2024. This reduction was primarily driven by a slight decrease in the share of the XMRig coinminer malware, following a similar trend from the previous quarter.
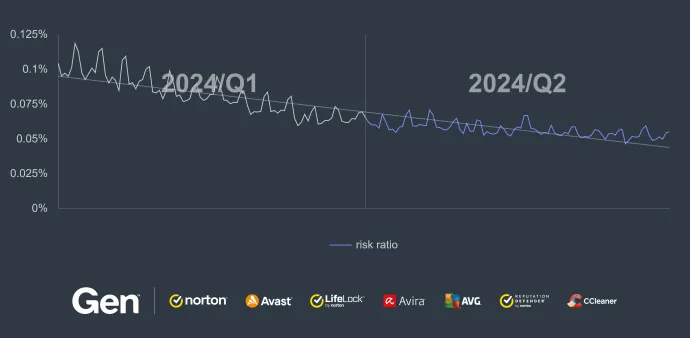
The decrease is mostly due to a significant drop in the United States and Turkey where the risk ratio of getting infected by a coinminer dropped by 34% and 38%, respectively. Brazil, India, and France also experienced drops in risk ratios by 5%, 16%, and 30%, respectively. The majority of countries saw a slight decline in coinmining activity over the quarter.
Hungary, on the other hand, bucked the trend with a 73% increase in the risk ratio in Q2/2024. This is particularly interesting because the increase is rather sporadic. The only other significant rise, among countries with a more substantial user base, is Slovakia, which saw a 14% increase in the risk ratio. Notably, Slovakia and Hungary are neighboring countries, creating an intriguing “hotspot.”
With that said, the highest risk ratios still prevail in Madagascar (1.9% risk ratio), Pakistan (1.19%), Turkey (0.91%), and Egypt (0.89%).
XMRig, the long-time leader in coinminer malware, saw its malware share decrease by 9% this quarter. Despite this decline, it still dominates with 53.89% of the total coinminer market.
Web miners, which include various JavaScript strains used for malicious background coinmining on webpages – either as raw malware or as an “alternative” to online advertising – have increased significantly by 20% compared to the previous quarter. Most other major coinminers also saw an uptick in activity. On the other hand, CoinHelper’s malware share dropped by 12% this quarter.
The most common coinminers with their malware share in Q2/2024 were:
- XMRig (53.89%)
- Web miners (24.32%)
- CoinBitMiner (2.97%)
- FakeKMSminer (2.12%)
- NeoScrypt (1.81%)
- CoinHelper (0.92%)
- VMiner (0.84%)
Jan Rubin, Malware Researcher
Information Stealers: with AgentTesla at Its Peak
Information stealers are dedicated to stealing anything of value from the victim’s device. Typically, they focus on stored credentials, cryptocurrencies, browser sessions/cookies, browser passwords and private documents.
According to our data, AgentTesla saw a new all-time in Q2/2024. Before we dive into numbers in the dedicated subsection, let’s have a look at a few campaigns that we observed during a busy April through June.
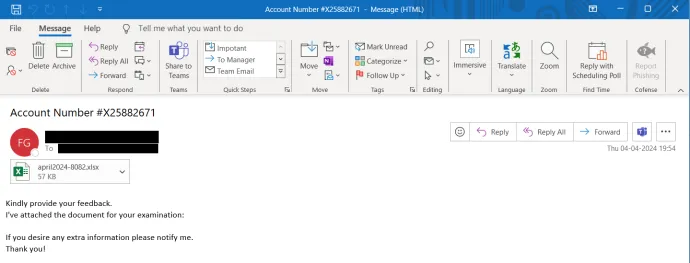
The major Information Stealer to highlight is AgentTesla. One of the major campaigns we identified targeted Czech users via emails disguised as legitimate orders. This particular campaign was also spreading Remcos RAT along with the notorious information stealer.
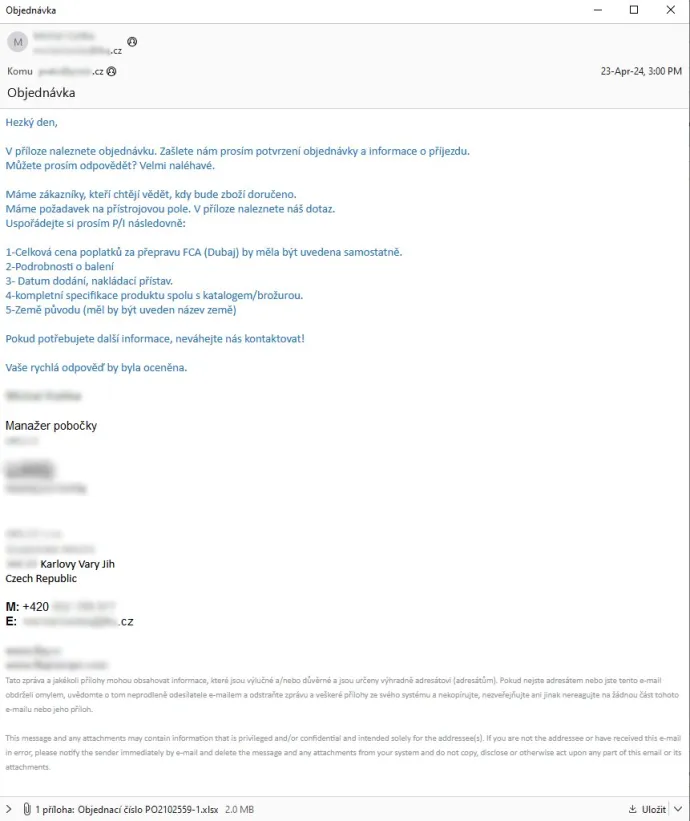
A fake-tutorial campaign, where attackers were distributing malicious PowerShell scripts via ClearFake, spread various information stealers including Lumma Stealer and attracted significant attention. This attack begins with social engineering, guiding the victim to follow a few simple steps to resolve a problem, in this case fixing Windows Update error 0x80070643, with the user ending up copying a script to their clipboard and pasting it into a command line or PowerShell console. After the script is executed, the victim is infected with a dropper, typically HijackLoader, distributing the aforementioned Lumma Stealer or other malware strains.
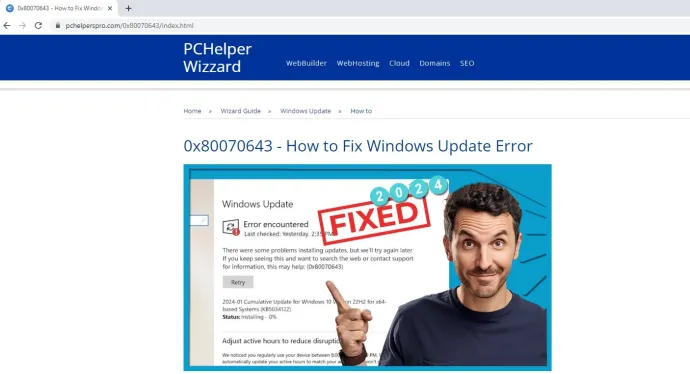
Interestingly, we also saw cases of the bad guys fighting for their reputation among the criminal underground – and in cases we saw, not so successfully. The author of DarkGate, using the nickname RastaFarEye, was banned on an underground forum a few months back due to some users raising complaints directed at this malware author.
Despite the ban and subsequent bad cybercriminal PR, we can still see new DarkGate builds with new features and continuous development. DarkGate is a long-standing information stealer with various RAT capabilities. In Q2/2024, there were multiple campaigns spreading DarkGate via malicious email attachments. The emails are crafted in such a way they lure the victim into downloading and opening the attachment, typically a MS Office document or a PDF file.
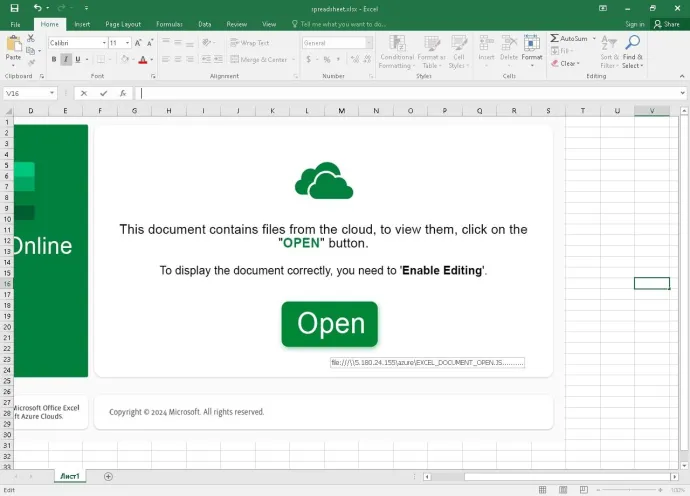
After the user opens the attached file, in this case a MS Excel XLSX file, they are presented with a message saying they need to “Enable Editing” and click the “Open” button to properly open the document. This effectively leads to infecting the victim with another stage of the malware, as can be seen in the image below as an IP address leading to a malware JavaScript file.
Now, thankfully some good news. Google is improving the security of Chrome cookies on Windows by implementing a new protection called Application-Bound Encryption. This Data Protection API (DPAPI) improvement effectively enhances protection against information stealers’ efforts to steal data from this popular web browser beginning with version 127. In short, for information stealers to steal the sensitive data, the malware will now need to either obtain system privileges or to inject itself into the Chrome browser, which are both noisy and more easily detectable actions by security solutions.
Statistics
In comparison with the previous quarter, the overall risk ratio of information stealers decreased once again in Q2/2024 by additional 11%. According to our data, this is due to a decrease in activity of mid-prevalent information stealers like Stealc, ClipBanker, or ViperSoftX. On the other hand, high-prevalent stealers like AgentTesla, Ramnit, FormBook, Vidar, Lumma, and others, increased their malware share.
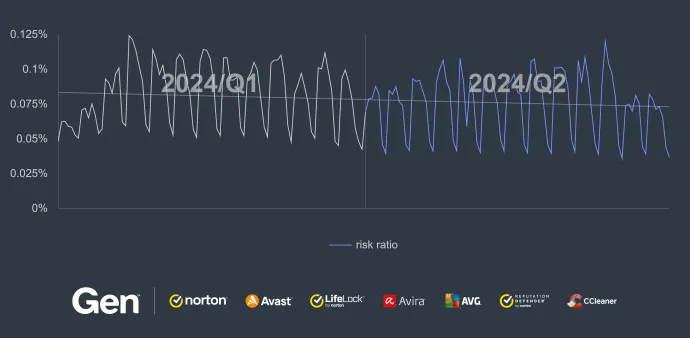
In countries where we have a more significant userbase, the risk ratio of getting infected by an information stealer thankfully decreased:
- Turkey (1.86%) with 18% Q/Q decrease
- Pakistan (1.76%) with 14% Q/Q decrease
- Egypt (1.55%) with 12% Q/Q decrease
However, there were also many countries more impacted than usual. For example, Nigeria had a risk ration increase of 130%, for a final risk ration of 2.28% risk ratio. In Ethiopia, the risk ratio increased by 48%, making 2.11% in total.
AgentTesla increased its malware share by 11% this quarter, further underlining its dominance in the information stealers landscape. The same goes with many other prevalent strains, like Ramnit (12% increase), FormBook (30% increase), Azorult (33 % increase), and Lokibot (59% increase). RedLine’s malware share decreased by 15%, similarly Fareit’s by 6%. ViperSoftX stayed roughly the same, with only a 2% decrease in malware share.
The most common information stealers with their malware shares in Q2/2024 were:
- AgentTesla (33.84%)
- Ramnit (12.04%)
- FormBook (9.05%)
- Fareit (7.10%)
- RedLine (3.67%)
- Vidar (2.70%)
- Azorult (2.56%)
- Lumma (2.44%)
- Lokibot (2.26%)
- ViperSoftX (2.22%)
Jan Rubin, Malware Researcher
Ransomware: The Wheels of Justice Turn Slowly, but Grind Exceedingly Fine
Ransomware is any type of extorting malware. The most common subtype is the one that encrypts documents, photos, videos, databases, and other files on the victim’s PC. Those files become unusable without decrypting them first. To decrypt the files, attackers demand money, “ransom”, hence the term ransomware.
The prevalence of ransomware within the consumer segment continues to be lower compared to past activity, but we have seen a significant +24% increase Q/Q with the highest increases in:
- India (up by 379%)
- United States, Canada, United Kingdom (all up by 100%)
- Australia (up by 66%)
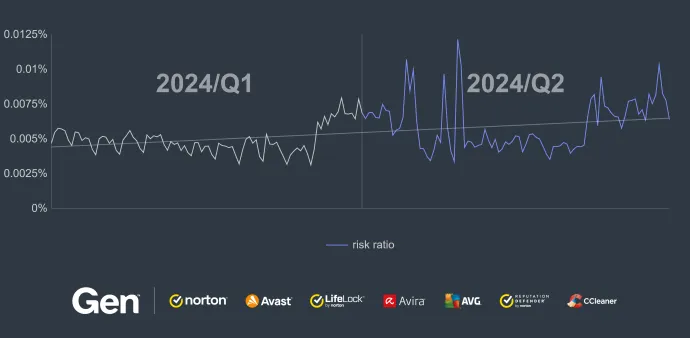
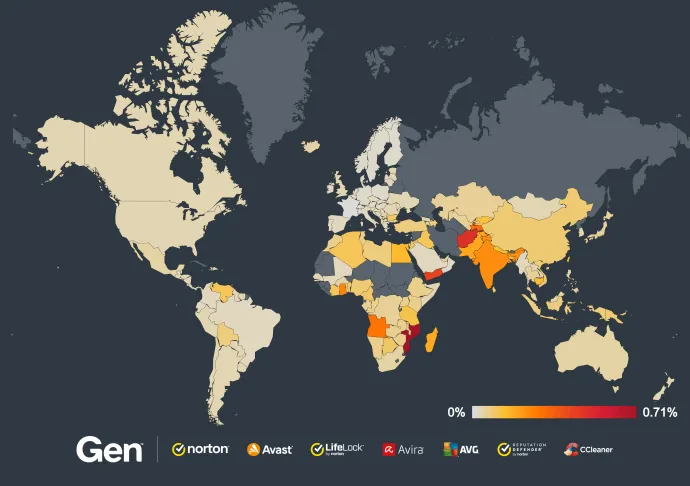
According to telemetry from our userbase, below are the most prevalent ransomware strains. The percentage values show the total market ratio of ransomware occurrence.
- WannaCry (21%)
- Cylance ransomware (9%)
- Enigma (8%)
- STOP (6%)
- LockBit (5%)
- Mallox (aka TargetCompany) (2%)
Justice for Ransomware Actors
Even though ransomware operators (like other cyber-criminals) are hiding their identity as much as possible, they may end up in the hands of the law in the end.
Example #1: Yaroslav Vasinskyi (Sodinokibi / REvil)
On the 1st of May 2024, Yaroslav Vasinskiy, one of the hackers in the REvil ransomware gang, was sentenced to 13 years and seven months in prison for his participation in the ransomware gang operation. According to the press release by the U.S. Department of Justice, Vasinskiy participated in about 2500 ransomware operations, demanding ransom payments of over $700 million. We do not know how much they actually earned, but Vasinskiy also must pay $16 million in restitution for the damage done.
REvil ransomware was one of the most successful ransomware operations in the history of computers. The most devastating operation was the Kaseya incident (more in Avast Threat Report Q3/2021), where the attackers abused a vulnerability in the Kaseya Remote Management software and deployed the REvil encryptor to thousands of companies.
REvil ransomware stopped their operation in 2022, and it is no longer active.
Example #2: Dmitry Yuryevich Khoroshev (LockBit)
6 days after the Vasinskyi’s sentence, the identity of LockBitSupp, administrator and developer of the LockBit ransomware group, was revealed to the public. He is Russian national Dmitry Yurievich Khoroshev (seen in the picture below).

Interestingly, two years earlier, Khoroshev was so sure of his anonymity that he offered a million-dollar reward to anyone who could send him his name and surname. Later, he increased that reward to $10 million.
We have been observing LockBit's activity over time and noticed that in the days immediately after the reveal of his identity, the number of attacked companies increased significantly. We can only speculate whether this was an act of revenge or pure coincidence.
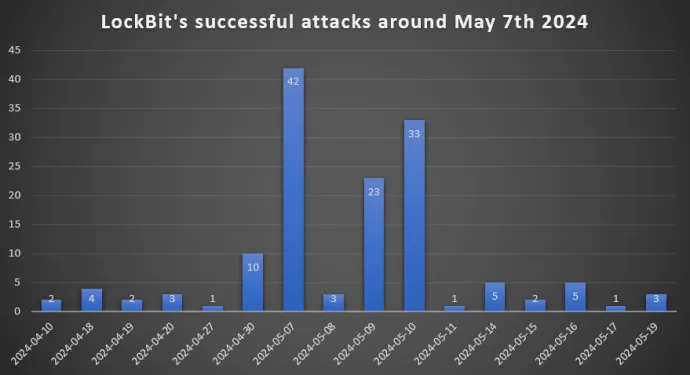
The question is what impact the identity reveal will have. The LockBit gang may start losing affiliates, which would mean decreasing its activity. Additionally, Khoroshev is now under sanctions (asset freeze and travel ban) in the US, UK, and Australian, so anyone who pays ransom in these countries could be considered in violation of these sanctions and subsequently imposed with a fine.
If you happen to know where he lives or can provide information leading to his arrest, you may earn up a nice money.
However, hackers in Russia are generally safe if they do not target companies belonging to Russia or any country in the Commonwealth of Independent States. So, until Khoroshev leaves Russia (or until the regime in Russia changes), he is probably safe.
Decrypted: DoNex
During Q2/2024, we discovered a weakness in the cryptographic schema of the DoNex ransomware and began silently cooperating with law-enforcement agencies to provide a decryptor to the victims. Since the details about the weakness were published in June at the REcon Montreal conference, we released the decryptor to the public.
The DoNex decryptor is just the latest in a series of ransomware decryptors we have developed for victims to use, free of charge.
Ladislav Zezula, Malware Researcher
Jakub Kroustek, Malware Research Director
Remote Access Trojans (RATs): The Takedowns Continue
A Remote Access Trojan (RAT) is a type of malicious software that allows unauthorized individuals to gain remote control over a victim's computer or device. RATs are typically spread through social engineering techniques, such as phishing emails or infected file downloads. Once installed, RATs grant the attacker complete access to the victim's device, enabling them to execute various malicious activities, such as spying, data theft, remote surveillance, and even taking control of the victim's webcam and microphone.
The dismantling of Remote Access Trojans (RATs) continued in Q2/2024, though we did not see the same high profile takedowns as we did with Warzone in the previous quarter. Although most major RAT strains seem to be hovering around or slightly below their numbers from the last quarter, Remcos picked up the pace keeping the overall risk ratio at the same level as in Q1/2024. The notable exception was Warzone, which suffered a large and expected decrease following its takedown.
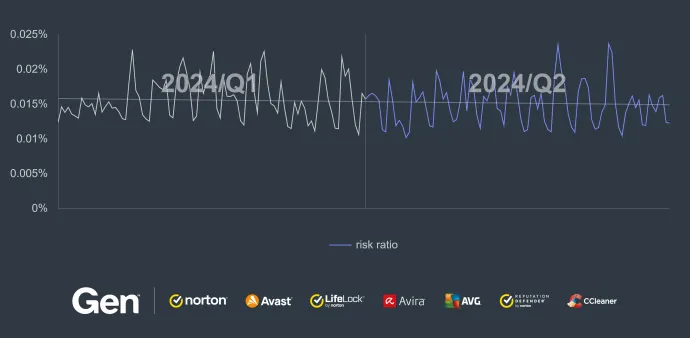
In Q1/2024, we reported XWorm as the most prevalent strain in Canada. This quarter, the risk ratio in Canada continued to grow (+52%) despite XWorm losing its malware share again to Remcos and AsyncRat. The biggest risk ratio increase was observed in Romania (+58%) with the third largest increase in Slovenia (+41%). Remcos is the main strain in all of these countries.
Greece (-27%), Spain (-23%) and France (-19%) saw the largest decreases in risk ration of RATs in Q2/2024. The decrease in Greece was due to AsyncRat while in Spain it was thanks to Remcos. The most interesting change was in France where we saw an increase of stopped attacks by Remcos but a decrease for all other strains such as AsyncRat, njRAT and QuasarRAT.
The countries with the highest overall risk ration globally remained consistent in Q2.2024 with Afghanistan, Iraq and Yemen in the lead with the most active threats being HWorld and njRAT.
As mentioned, Remcos gained a significant share of the RAT market in Q2/2024 with a 34% increase, the most of all RAT strains we monitor. DarkCrystal also increased its malware share by 28% bringing it closer to the overall top 10.
The takedown of Warzone in Q1/2024 continued to impact its share numbers with an additional loss of 39% of the market in Q2/2024, with additional decreases expected in the future.
The most prevalent RAT strains for Q2/2024 are as follows:
- Remcos
- HWorm
- njRAT
- AsyncRat
- QuasarRAT
- XWorm
- FlawedAmmyy
- Warzone
- NanoCore
- Gh0stCringe
Q2 Takedowns
This quarter, an operation against two individuals involved in RAT creation and distribution was carried out jointly by the AFP (Australian Federal Police) and the FBI (Federal Bureau of Investigation). The AFP arrested an Australian man alleged to have developed and sold the Firebird RAT. The FBI then seized another US-based man suspected of advertising and selling the RAT as well as providing customer support. Firebird, later rebranded to Hive, is a RAT which has been active for several years but was never very widely spread. According to our data, only a small number of attacks were performed (and blocked) in our userbase in Q2/2024.
Lastly, Cisco Talos uncovered a new RAT called SpiceRAT which, according to their research, is used by the SneakyChef threat actor. SpiceRAT is not a full-featured RAT like Remcos or AsyncRat. Its role is to serve as an entry point for additional plugins or further attacks. The basic capabilities include fingerprinting the system, downloading and running executable binaries and executing commands.
Ondrej Mokos, Malware Researcher
Vulnerabilities and Exploits
Exploits take advantage of flaws in legitimate software to perform actions that should not be allowed. They are typically categorized into remote code execution (RCE) exploits, which allow attackers to infect another machine, and local privilege escalation (LPE) exploits, which allow attackers to take more control of a partially infected machine.
In Q2/2024, several significant vulnerabilities were discovered and exploited, posing serious risks to systems and users. In this section, we highlight the most prevalent for the quarter.
Windows DWM Core Library Vulnerability CVE-2024-30051
In early April 2024, Kaspersky discovered a peculiar document uploaded to VirusTotal. The document's file name suggested it contained information about a Windows OS vulnerability. Upon examination, they found a description of a Windows Desktop Window Manager (DWM) vulnerability and its potential for privilege escalation.
What they discovered is a heap-based buffer overflow vulnerability affecting the Windows DWM Core Library that can be exploited to elevate attacker’s privileges on a targeted system. Kaspersky researchers have connected this zero-day vulnerability to Qakbot and various other types of malware.
CrushFTP Zero-Day Vulnerability
CrushFTP, a vendor specializing in managed file transfer solutions, disclosed a critical zero-day vulnerability. This flaw affects CrushFTP versions below 10.7.1 and 11.1.0, as well as legacy 9.x versions across all platforms.
This vulnerability is a VFS (Virtual File System) sandbox escape. The flaw allows remote attackers with minimal privileges to read files outside of the VFS Sandbox. Exploiting this vulnerability can lead to arbitrary file reads with root privileges, bypass authentication to gain administrator access, and execute remote code. Consequently, an attacker could access and potentially exfiltrate all files stored on a CrushFTP instance.
New trick uses old Internet Explorer vulnerabilities (CVE-2024-38112)
Check Point Research has uncovered a clever new tactic used by attackers to trick Windows users into executing malicious code. The attackers are exploiting a vulnerability involving Windows Internet Shortcut files (.url). These files, when clicked, use the outdated Internet Explorer (IE) to visit a URL controlled by the attackers, even if the victim's computer is running modern Windows 10 or 11.
EchoSpoofing: Unmasking a Massive Scam Campaign Exploiting Proofpoint's Email Routing Misconfiguration
According to a Guardio Labs researcher, the recent campaign exploited an email routing loophole within Proofpoint’s infrastructure, allowing the attackers to send millions of emails daily. These emails, authenticated with Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) signatures, bypassed major security protections, making them appear legitimate and enabling the threat actors to steal funds and credit card details from unsuspecting recipients.
This attack, called EchoSpoofing, involves the threat actor sending messages from an SMTP server hosted on a virtual private server (VPS). The scam's effectiveness lies in its ability to comply with security measures such as SPF and DKIM, which are designed to prevent attackers from imitating legitimate domains. These spoofed messages are routed through various adversary-controlled Microsoft 365 tenants, then relayed via Proofpoint's customer email infrastructures to reach end-users of free email providers like Yahoo!, Gmail, and GMX.
The EchoSpoofing campaign is believed to have begun in January 2024, with the threat actor sending an average of three million emails daily. However, the volume spiked to a staggering 14 million messages per day in early June as Proofpoint started implementing countermeasures. The attackers used a cracked version of legitimate email delivery software called PowerMTA, combined with rotating VPS servers and IP addresses, to send massive bursts of emails from their SMTP servers.
Proofpoint has acknowledged the scale of the threat, stating that it does not overlap with any known threat actors or groups.
Luigino Camastra, Malware Researcher
Michal Salat, Threat Intelligence Director
Web Threats
In our ongoing effort to stay ahead of the evolving threat landscape, we rapidly adapt to emerging infection vectors, which are now often web-related. Those familiar with our reports will recognize how significantly the web threats section has expanded over time. From Q4/2023 to Q2/2024, web threats have seen an approximate 17% increase in incidents compared to other cyber threats, underscoring a persistent and troubling upward trend.
Overall, as we approach the end of Q2, a small but noticeable decline in general web threat activity can be observed. We believe that this decrease is largely attributed to the onset of summer holidays, a period when both cybercriminal activities and online engagements often reduce due to seasonal changes in user behavior and routines.
At the same time, the core scam threats are still strong and very prevalent in our userbase. As we will show shortly, there was a significant increase in financial scams such as Crypto Scams fueled by CryptoCore as well as enhanced Part-Time Job Scams (aka Task Scams). Dating Scams and Technical Support Scams are also not disappearing anytime soon based on their strong Q2/2024 presence. Lastly, we will showcase an example of another prevalent threat – Fake Invoice Scams.
Scams: Assessing the Real Risk vs. Reward
A scam is a type of threat that aims to trick users into giving an attacker their personal information or money. We track diverse types of scams which are listed below.
Scam threats, which are often supported by malvertising, had their highest activity at the beginning of Q2/2024. After that, we observe a slight decline in overall prevalence.
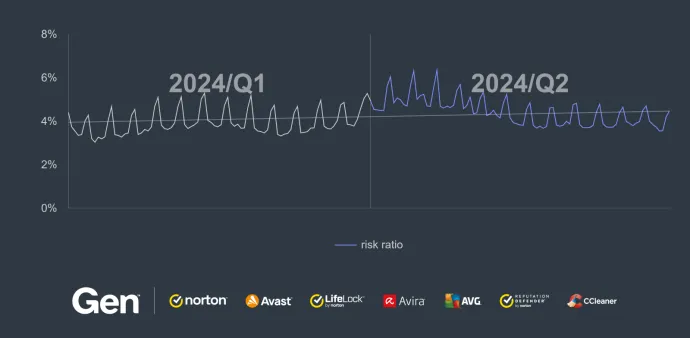
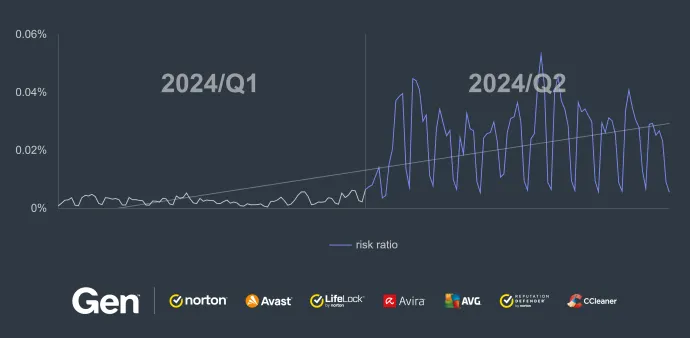
The small decrease in activity is only relative and often caused by threat actors switching between various scam schemas. We are continuously improving our threat insight and reflecting such changes in the threat landscape. One such situation happened within the Financial Scams in Q2/2024, which is visible on the following chart depicting our insight.
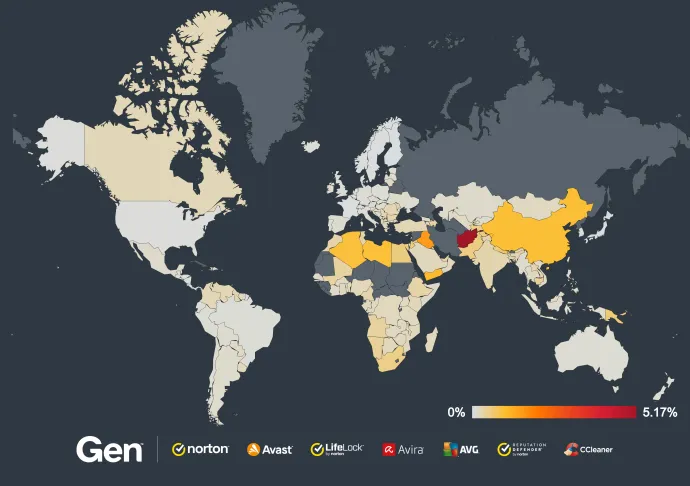
In terms of the Financial Scams in Q2/2024, the most impacted countries were New Zealand, Czech Republic, all the Nordic countries, but also Canada, Australia, and the UK.
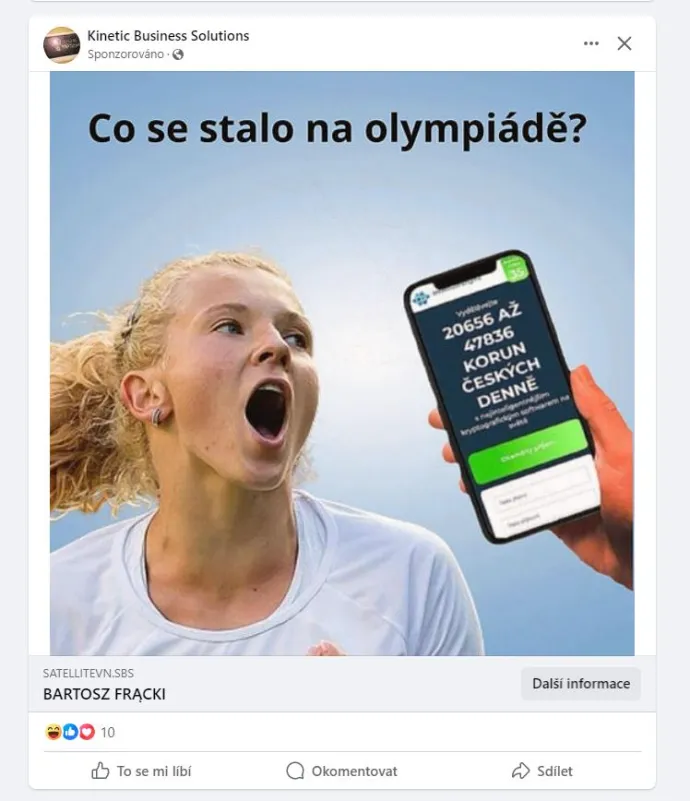
We frequently write about the principle of this particular scams, which commonly leverages paid ads on social platforms. These advertisements are becoming increasingly innovative. As noted in our previous report, scammers are now using deepfake technology and enlisting various celebrities of the different regions in order to better target users. Additionally, they often employ sensationalist headlines to draw attention. It doesn't always have to be just about celebrities, sometimes they take advantage of the action, like the recent summer games in France.
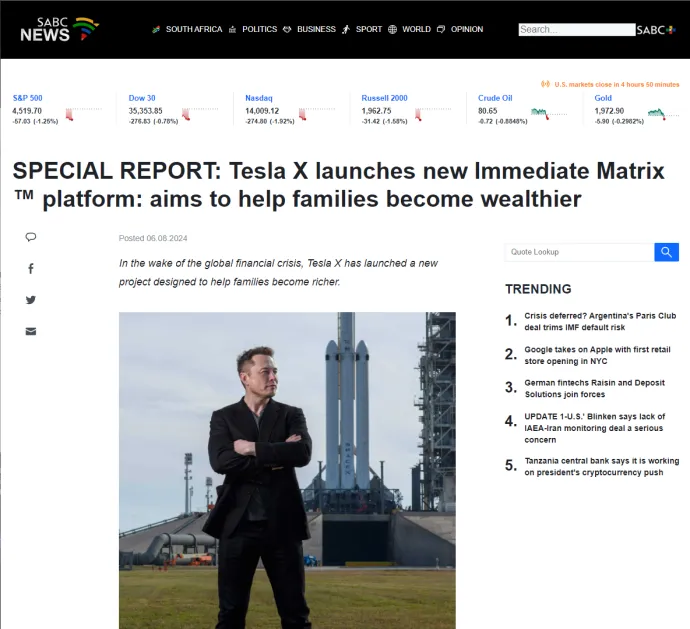
After clicking on the advertisement, the user is redirected to a prepared scam page, where the content of the ad is then supported by, for example, a fake news page or a form where the user has to fill in specific personal data.
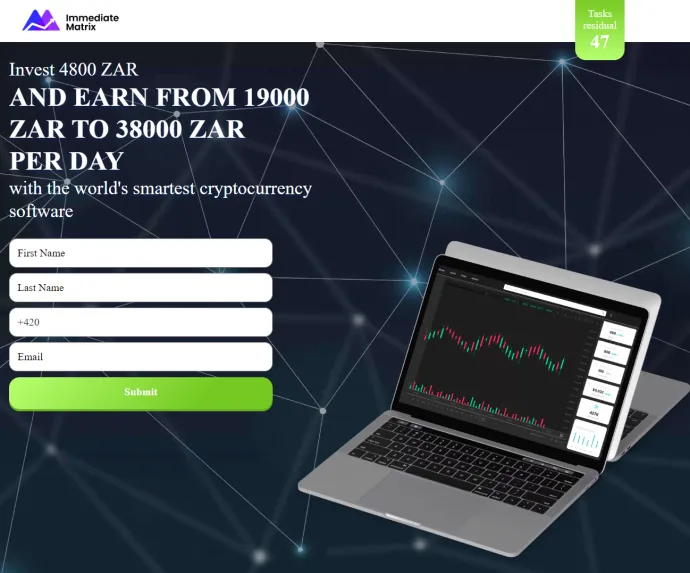
Attracting users to money doesn't only work in the context of investments, this will surely only attract some people. But what about, for example, putting the possibility of making money in a different context. This is dealt with in the next section.
Part-Time Job Scams: A Growing Threat with New Tactics
The allure of easy money, especially during difficult economic times, can lead many into the trap of Part-Time Job Scams. These scams, often initiated through messaging platforms like WhatsApp and Telegram, have evolved into more sophisticated operations that exploit victims using social engineering techniques. Scammers promise simple online tasks in exchange for steady income, but the ultimate goal is to steal large sums of money from unsuspecting victims.
The New Phone Call Tactic
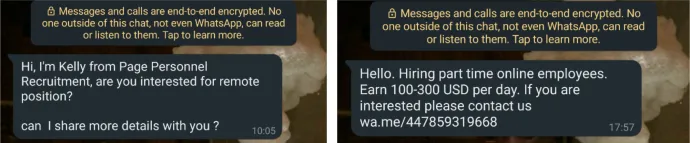
A recent development in these scams is the use of phone calls to initiate contact. Scammers now employ a natural-sounding feminine voice, likely generated by AI, to inform potential victims that they have been selected for a reward, such as a $5 TikTok voucher. The victim is then instructed to add the calling number to their contacts and continue communication via WhatsApp. Here’s an example of how the conversation unfolds in WhatsApp:
Real Example of a WhatsApp Conversation with the Scammers:
Scammer: Hello, my name is XXXXXX. Can I talk to you for 2-3 minutes?
Victim: Yes, of course.
Scammer: Thank you for your response. Our company works with TikTok merchants who are willing to pay to increase subscriptions and the visibility of bloggers. Therefore, our company needs to hire many coworkers to increase subscriptions for them on the TikTok app, and they will pay you.
Scammer: We need many people to participate in the short video promotion bonus event and like TikTok content. Each video can earn you a reward of 3 euros, and you can earn a reward of 300-800 euros every day.
Scammer: Are you interested in working with us?
Victim: Yes, of course.
Scammer: How old are you? Do you have a Telegram application?
Victim: I am 28 years old and yes, I have Telegram.
Scammer: Okay, very well. This is the easiest part-time job, just go to the link (TikTok), like the video, take a photo, and send it to us.
(The victim completes the task and sends the screenshot)
Scammer: Well done. I think you already know how we work. I will give you 3 TikTok video links as a test. You don’t need to watch the entire video, just like it and send me a screenshot, and you will earn 3€.
(Victim does the tasks and shows the screenshots)
Scammer: Okay, I think you know how we work. Please add our business manager on Telegram:
https://t.me/scammer_handle (link to scammer’s Telegram chat)
Your employment code: XXXXXXX
Scammer: Contact the recipient now, send him the code to fill out your details and you can earn 5€ for a total of 8€. Many people are in line to participate, please wait patiently, the receptionist will receive you. Please complete your information and submit it, after which you will receive a payment.
Going Undercover: Uncovering the Scam
To better understand the operation, we went undercover, engaging in one of these scams. We were asked to perform simple tasks, such as adding products to an eBay shopping cart and sending screenshots as proof. Initially, the scammers deposited a small amount of USDT cryptocurrency into our wallet, which we could verify in our account. This tactic is used to build trust and lend legitimacy to the scam.
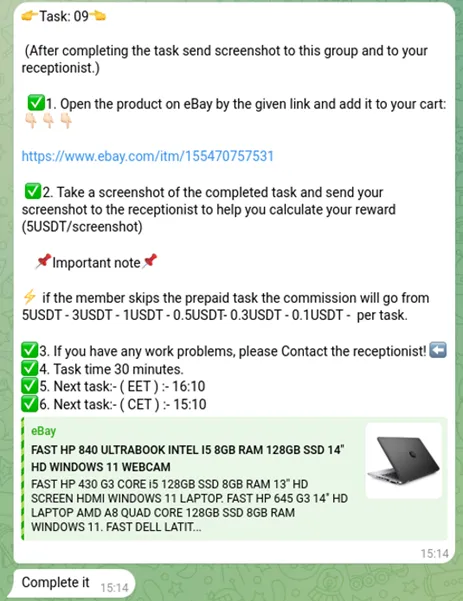
However, the true nature of the scam was revealed when we were invited to participate in a ‘VIP’ task, promising a significant return on an upfront investment. We were added to a larger group chat that appeared to be bustling with activity—many users were requesting tasks and submitting proof of receiving payments. It quickly became evident that most of these accounts were fake, likely bots, designed to create a false sense of legitimacy.
When victims make a significant deposit for these VIP tasks, the scammers vanish, taking the money with them. Often, they might attempt to extract even more money by inventing additional fees or taxes, all while threatening the loss of the initial investment.
Impact and Scope
These scams are becoming increasingly prevalent, with reports of significant financial losses. According to recent data from the Federal Trade Commission (FTC), investment-related scams saw a 14% increase in losses, amounting to over $10 billion in 2023 alone. The global reach of these scams is evident, with cases reported in multiple languages, including English, Spanish, and Czech. The use of AI-generated voices adds a new layer of deception, making these scams harder to detect.
Crypto Scam Powered by CryptoCore
A crypto scam is a cyber threat designed to trick individuals into surrendering their cryptocurrency. These scams exploit the anonymity and irreversibility of blockchain transactions, often targeting those with a limited understanding of how cryptocurrency works.
Also in Q2/2024, we followed a crypto scam group, we dubbed CryptoCore, that lures individuals with promises of high returns or uses sophisticated schemes to defraud even the most cautious via deepfake videos to convince victims of unique cryptocurrency investment opportunities. These deepfake videos exploit famous personalities and brands such as Elon Musk, Michael Saylor, Donald Trump, BlackRock, and Apple to enhance trust and legitimacy. Scam videos are primarily spread on popular platforms like YouTube, X, and TikTok through hacked accounts, exploiting hundreds of accounts with many subscribers. Consequently, the total revenues from these scams amount to millions of dollars in various cryptocurrencies.
The initial phase of the scam involves targeting widely publicized events that will be broadcast live to draw a large audience. The scammers then produce deepfake videos replicating official event footage and including QR codes directing viewers to fraudulent websites. These scam videos are disseminated through compromised accounts on major platforms, especially YouTube. The campaign's effectiveness leads to the accumulation of cryptocurrency in fraudulently obtained wallets.
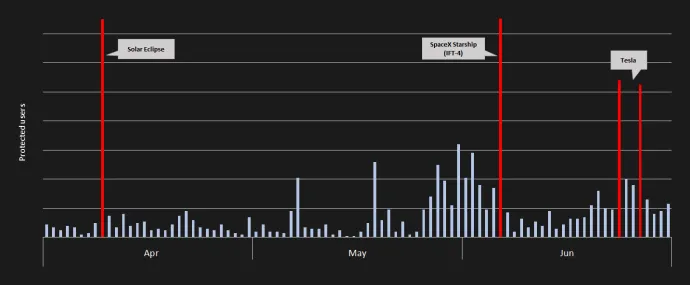
In Q2/2024, our telemetry identified three significant events related to this crypto scam. The first occurred on April 8, 2024, during the solar eclipse, when SpaceX's name was exploited. The second campaign was on June 6, 2024, during the SpaceX Starship integrated flight test (IFT-4). Within several days, nearly 50 YouTube accounts were hijacked, and we identified 500 transactions, amounting to a total value of $1.413 million, in this campaign. The last one was at the end of June 2024, when the Tesla band was abused in the crypto scam.
The complete analysis can be found in our article.
Dating Scams: Cyber Criminals Still Love Them
Dating scams, also known as romance scams or online dating scams, involve fraudsters deceiving individuals into fake romantic relationships. Scammers adopt fake online identities to gain the victim's trust, with the ultimate goal of obtaining money or enough personal information to commit identity theft.
The prevalence of Dating Scams has remained consistent, with no significant change in their occurrence or methodology in Q2/2024. Scammers continue to exploit emotional connections to deceive victims, employing tried and true tactics that have proven effective over time. This steadfast activity highlights the ongoing need for vigilance and education in recognizing and avoiding such deceptive practices.
The screenshot below shows a landing page that users reach after clicking on a push notification designed to lure them to join a fraudulent dating site. This page cleverly prompts visitors to sign up, exploiting their search for companionship with promises of easy connections and potential matches.
Such pages often use engaging visuals and persuasive language to lower users' defenses and encourage registration, making it crucial to approach such sites with caution and skepticism.
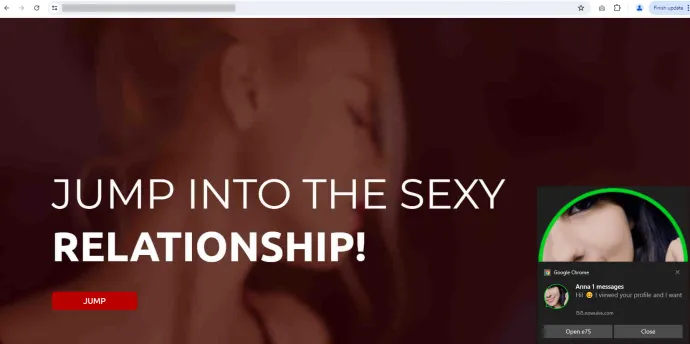
Compared to Q1/2024, the highest increase of Dating Scam risk was seen in Japan (+51%). However, the top 10 countries at risk were all from Europe in Q2, led by Norway, Denmark, Poland, and Germany.
Tech Support Scams: No Slowdown in Sight
Tech support scam threats involve fraudsters posing as legitimate technical support representatives who attempt to gain remote access to victims' devices or obtain sensitive personal information, such as credit card or banking details. These scams rely on confidence tricks to gain victims' trust and often involve convincing them to pay for unnecessary services or purchase expensive gift cards. It's important for internet users to be vigilant and to verify the credentials of anyone claiming to offer technical support services.
Tech Support Scams (TSS) have maintained their increased activity from the from Q1/2024 through a significant portion of Q2/2024. This activity, as the graph below indicates, started to decrease slightly towards the end of the quarter.
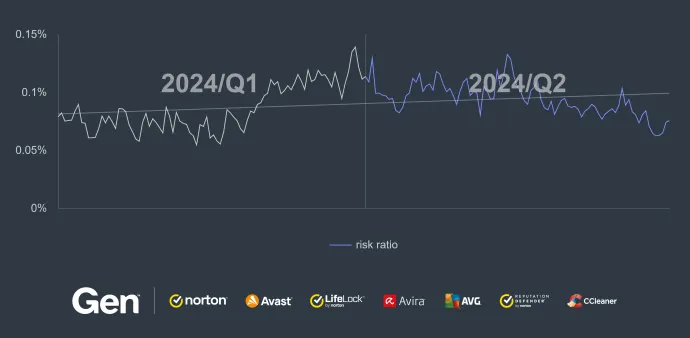
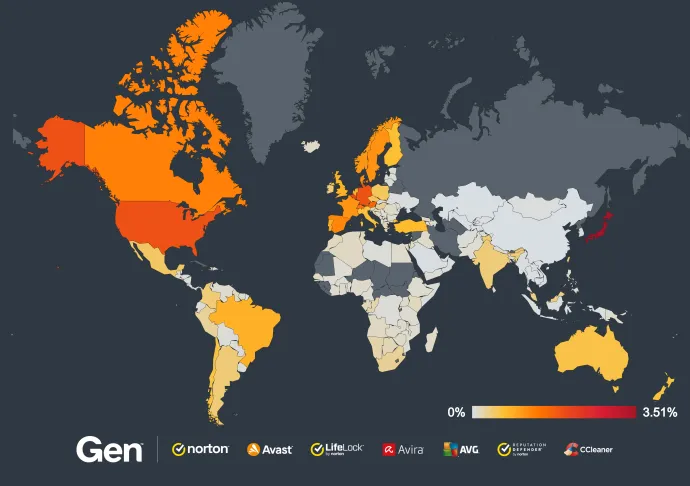
Japan, the United States, and Germany remain hot spots for this TSS Scam threats.
Refund and Invoice Scams: Persistent Presence
Invoice scams involve fraudsters sending false bills or invoices for goods or services that were never ordered or received. Scammers rely on invoices looking legitimate, often using company logos or other branding to trick unsuspecting victims into making payments. These scams can be especially effective when targeted at businesses, as employees may assume that a colleague made the purchase or simply overlook the details of the invoice. It's important to carefully review all invoices and bills before making any payments and to verify the legitimacy of the sender if there are any suspicions of fraud.
In Q2/2024, Invoice Scams have shown no sign of decreasing, even with the start of the summer holidays. Although the number of attacks has fluctuated slightly, the overall trend remains steady with no significant decline expected in the near future. However, a closer look at the data reveals notable changes on a country-by-country basis, with Australia and Greece experiencing the most significant quarter-on-quarter increases.
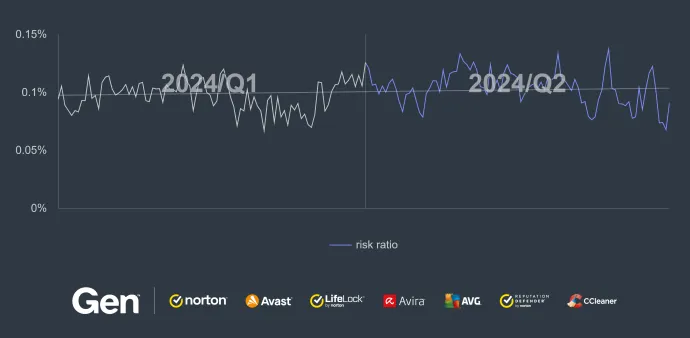
Overall, Australia, the United States, the Netherlands, the United Kingdom, and Canada were countries most at risk against fake Refund and Invoice Scams. Greece experienced a nearly 28% increase in the number of protected users, with Australia and Cyprus following at 24% and 17%, respectively. This signals a rise in targeted activity. Conversely, Vietnam saw the largest decrease, with a 66% decline, followed by Argentina and Egypt, both at 50%. What trends have emerged in these scams recently? Let’s examine a real-life example that could find its way into your inbox.
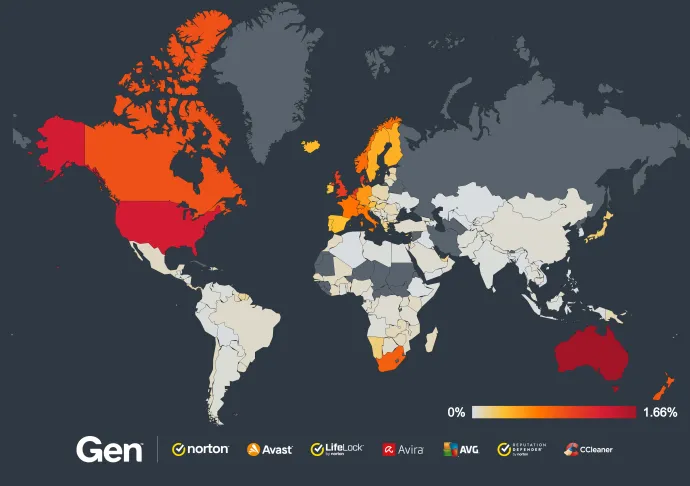
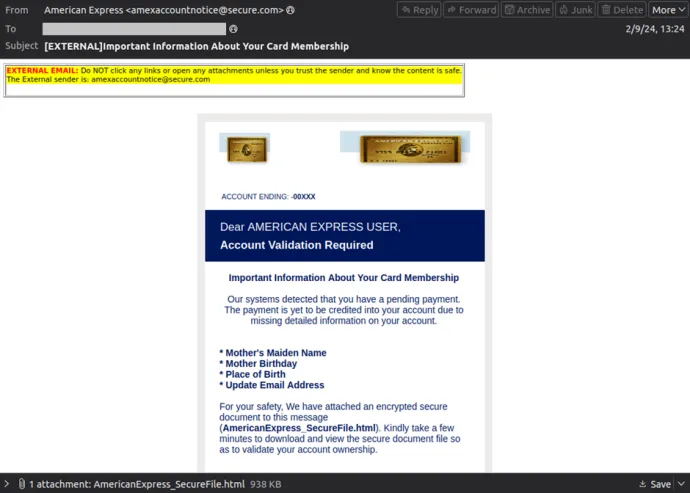
Among the numerous scams we've encountered recently is one specifically targeting a prominent antivirus company. The phishing email appears like the one shown below:
Here are five key red flags in the email that indicate it is likely a phishing attempt or scam:
- Suspicious Sender Domain: The email is sent from a domain that does not match the official product domain, instead using a questionable domain like adrenaline.xambassadors.com, which is unrelated to the company.
- Urgent Time Pressure: The email creates a false sense of urgency, claiming your account will be deleted in "48 hours" if you don't take immediate action. This is a common tactic used in scams to pressure you into acting without thinking.
- Poor Design and Layout: The email's design is simplistic and unprofessional, lacking the polish typically seen in legitimate company communications. The layout is awkward, with excessive use of red and bold text, which is often a hallmark of scam emails.
- Weird Template and Content: The content and structure of the email, including phrases like "Restoration code" and odd formatting, don't align with how a legitimate antivirus company would communicate with its customers.
- Unusual Font in the Subject Line: The subject line uses strange characters and symbols (e.g., "⚠️ Final Warning ⚠️"), which is not typical for professional emails. This is often done to grab attention but is a clear indicator of a potential scam.
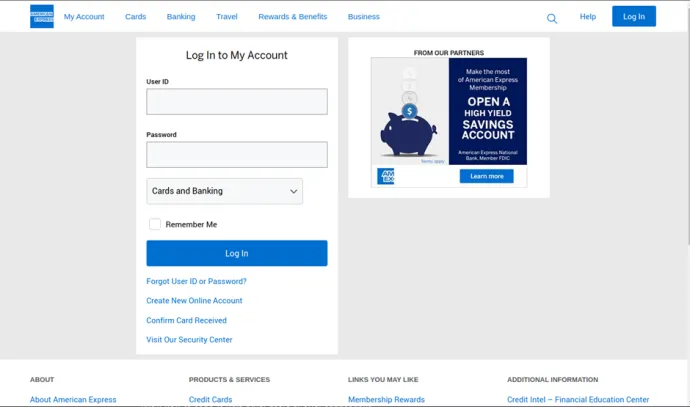
Now, let's explore where the rabbit hole leads. The prominent button you’re tempted to click, labeled "Activate Now" with the threat of account deletion, is a tactic to create urgency, which is entirely false. Clicking this button triggers a redirection chain, starting with the following URL. Other parameters, likely tailored based on your location and other factors, determine where you will end up.
https://storage.googleapis[.]com/bazugza/SalXX0134.html#u8sf8ls.ETbnaSCDpu?xpxwrvtnegfg=raemsgaddlde1g3qefg004w3k002jit020330b04735080cxq
Which will redirect you to:
bonusmonster[.]co

This is the landing page you encounter if you are in the United States. The actors likely use redirection based on various factors, including your country of residence. The page bears no resemblance to the official product website, or anything related to the company. You will not obtain anything for free from this site. After conducting further investigation, we found that the domain is hosted on:
172.67.137[.]213
We were interested in finding out what other domains are hosted on this IP address and used VirusTotal to gain more insight into the nature of this server. Here’s what we discovered:
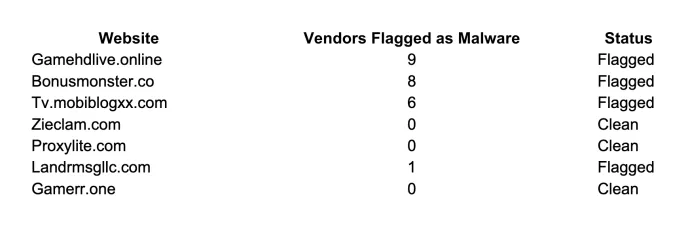
The IP address 172.67.137[.]213 is linked to several websites, including some flagged for malware like Gamehdlive[.]online, Bonusmonster[.]co, and Tv.mobiblogxx[.]com, with Bonusmonster[.]co specifically accessed through a scam email. While sites like Zieclam[.]com, Proxylite[.]com, and Gamerr[.]one seem to be clean, the high number of flagged sites indicates a significant risk of malicious activity associated with this IP address.
The lesson here is clear: the threat of cyberattacks remains persistent, and staying vigilant is essential. Remember, legitimate companies will never demand immediate action with threats of losing your data or account. Always take your time when reviewing emails, carefully checking the sender's details and evaluating the overall legitimacy of the message. By maintaining this cautious approach, you can better protect yourself from phishing attempts and other online threats.
Bank Phishing: A Growing Concern
Phishing is a type of online scam where fraudsters attempt to obtain sensitive information including passwords or credit card details by posing as a trustworthy entity in an electronic communication, such as an email, text message, or instant message. The fraudulent message usually contains a link to a fake website that looks like the real one, where the victim is asked to enter their sensitive information.
Similar to Dating Scams, the situation with phishing threats remains stable with a slight calming of activity before the end of Q2/2024.
One of the interesting things in the phishing category has been the growing number of new bank phishing sites. In our data, we see that not only are the most popular banks being targeted but there are more sites dedicated to lesser-known banks that were not targeted in the past. We also see increased amounts of new variants of the phishing kit.
One notable incident from the start of the quarter involved a phishing campaign in the United States targeting Bank of America users. This operation aimed to deceive users into disclosing their personal banking information by mimicking official communications from the bank, a tactic that underscores the persistent risk in the financial sector.
These phishing campaigns typically show a short lifespan. According to our data, on its most successful days, this particular campaign targeting Bank of America users received high hundreds of hits per day, highlighting the possible effectiveness of these threats.
Alexej Savcin, Malware Analyst
Branislav Kramar, Malware Analyst
Matej Krcma, Malware Analyst
Martin Chlumecky, Malware Researcher
David Jursa, Malware Researcher
Mobile-Related Threats
We observed several new strains of mobile malware in Q2/2024 with interesting new techniques being deployed in both delivery and functionality. Notably, a clicker adware has snuck onto the PlayStore, clicking on websites in the background and gathering fraudulent advertising revenue.
In the world of bankers, a dormant PDF reader application on the PlayStore also came to life this quarter, turning into a TeaBot banker dropper and targeting Revolut accounts of its victims. A new banker called SoumniBot entered the fray, with several new obfuscation techniques and the ability to steal Korean bank certificates. An updated version of the Medusa banker used botnets in France, Spain and Italy to distribute its malicious payload, in some cases pretending to be the Avast Premium app.
In the spyware category, we see more targeted campaigns, with XploitSpy utilising GitHub and PlayStore to target victims in India and Pakistan, stealing sensitive information. And finally, AridSpy has been seen targeting users in Egypt and Palestine with a heavily intrusive feature set capable of taking photos every hour and listening to surrounding audio.
Web Threat Data within the Mobile Landscape
Most blocked attacks on mobile devices in Q2/2024 were web-based, mirroring the previous quarter. Users are much more likely to encounter phishing websites, scams, malvertising and other web threats than ever before. These threats can come in a variety of formats such as private messages, SMS, and emails but also redirects on less reputable sites, unwanted pop ups and through other avenues.
In contrast to these types of mobile scams, traditional on-device malware requires a more complex infection vector where the user must also install the malware. For proper functionality of most mobile malware, permissions need to be granted by the user first, which again lowers the chances of malicious activity being triggered.
Hence, blocking web-threat based attacks is beneficial for the security of mobile devices, as malware actors often use them as an entry point to get the payload onto the mobile device of their victims.
Adware: Sneaky Clickers on the PlayStore
Adware threats on mobile phones refer to applications that display intrusive out-of-context adverts to users with the intent of gathering fraudulent advertising revenue. This malicious functionality is often delayed until sometime after installation and coupled with stealthy features such as hiding the adware app icon to prevent removal. Adware mimics popular apps such as games, camera filters, and wallpaper apps, to name a few.
With another quarter behind us, adware retains its top place as on-device malware in the mobile threat ecosystem. Most prevalent for several years now, it is a threat that spreads through various forms of malvertising, third-party app stores and it occasionally manages to sneak onto the PlayStore. Once installed, it negatively affects the user experience by clogging the device with fullscreen adverts and raking in fraudulent advertising revenue.
HiddenAds continue to be the adware with most reach in Q2/2024. As per their name, they hide their presence on the victim’s device once installed, then display intrusive full screen advertisements to the annoyance of their victims. MobiDash and FakeAdBlockers are the other prevalent strains that are often disguised as repacked popular games or paid applications but instead come with out of context adverts.
A new strain of Clicker adware has made its way onto the PlayStore, disguised inside both a fitness and adult application. These apps contain two hidden modules, one which collects extensive information on the device and user, while the other simultaneously loads webpages in the background. Once the pages are loaded through a hidden WebView browser window, the Clicker injects JavaScript code downloaded from a C&C so it can silence pages with videos or audio and look for advertisements to click on with the intent of gathering fraudulent advertising revenue. It is even able to take secret screenshots of the hidden webpages and determine clickable areas from these. It is curious that these advanced techniques were used to merely gather advertising revenue.
We observe a downward trend in risk ratio of adware this quarter. All three of the most prevalent strains continue to see a decrease in risk ratio and protected users. We may see a slight increase in the next quarter if more adware slips onto the PlayStore.
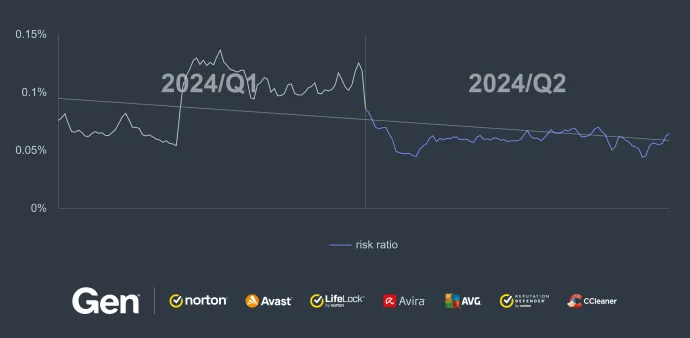
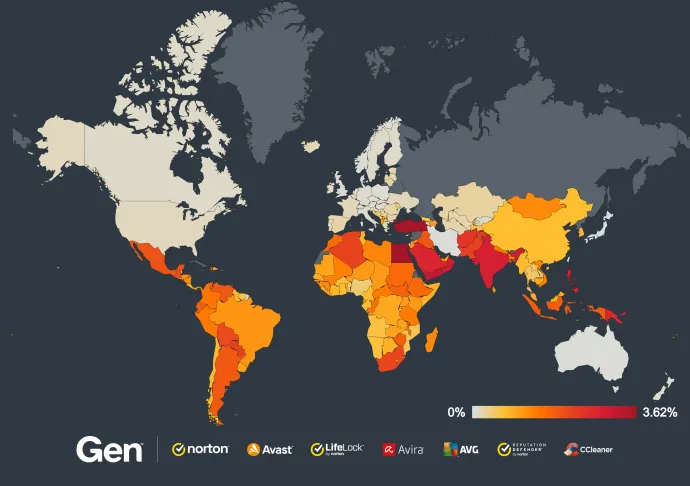
Brazil, India and Argentina again have the most protected users quartering Q2/2024, as was the case last quarter. According to our telemetry, Egypt, Turkey and Yemen have the highest risk ratios, meaning users are most likely to encounter adware in these countries.
Bankers: Never-ending Evolution Continues
Bankers are a sophisticated type of mobile malware that targets banking details, cryptocurrency wallets, and instant payments with the intent of extracting money. Generally distributed through phishing messages or fake websites, Bankers can take over a victim's device by abusing the accessibility service. Once installed and enabled, they often monitor 2FA SMS messages and may display fake bank overlays to steal login information.
Mobile bankers continue to evolve and threat actors bring in new strains to extract money and sensitive information from victims this quarter. The TeaBot banker spreads through a dropper on the PlayStore, targeting Revolut accounts. A new contender, SoumniBot, targets Korean users with various advanced obfuscation techniques. BrokeWell is another new banker that spreads through fake Chrome update pages. Finally, we see an evolution of the Medusa banker with botnets in various countries.
Our data shows that the RewardSteal banker takes first place this quarter, almost doubling its presence, mostly focusing on India. It is followed by Coper banker which also sees a big spike in prevalence with updates to its distribution methods. Of note is the MoqHao banker mentioned in the last report, it has continued to increase its presence this quarter as well, targeting victims in Japan and Korea.
Teabot banker makes a comeback with a dormant dropper going active on the PlayStore to deliver the malicious payload. Disguised as a PDF reader, the dropper went live in February with a sneaky update. It would first download an external DEX file and execute it, then perform various checks on the device to ensure it is not being emulated. It would only deliver the TeaBot payload to specific countries, such as Czech Republic, Slovakia, United Kingdom, Spain and surprisingly even Russia, which has been previously excluded by TeaBot. If it deemed the device viable, it would push a notification with a fake ‘PDF AI update available’ dialogue.
Once downloaded and installed, it would initiate device takeover through the accessibility service to extract banking details and steal money from victims. Interestingly, the banker specifically focuses on the Revolut app, querying the victim’s balance and information for further nefarious activity.
There was also a new arrival on the banker scene in Q2/2024, with SoumniBot marking its entrance. Bringing in various obfuscation techniques and exploiting bugs in the Android manifest extraction and parsing procedure, it aims to avoid analysis and detection. It utilizes an invalid compression method value to essentially break the manifest file for all but the APK parser on devices, which can still open and install the application correctly. Furthermore, it uses invalid manifest size to break stricter parsers but allows the on-device parser to run it correctly. Finally, it contains long namespace names that make it more difficult to analyze for threat analysts. Once installed, it extracts contact lists, SMS messages and device IDs. It is also able to receive further instructions from the threat actors, such as sending photos, videos and adding or deleting contacts on the device among others. The banker mostly targets Korea and extracts digital online banking certificates used for online banking and approving transactions, which is a fairly unique feature.
BrokeWell banker also joined the fray, spreading through fake Chrome update pages. Once installed, it can display fake bank overlay pages to extract login data, as well as run its own WebView with the intent of stealing session cookies and sending them to a command and control (C&C) server. Through the accessibility service, BrokeWell monitors its victims' every move and swipe while sending records to a C&C. The threat actors can also initiate a device takeover and perform actions such as swiping, tapping and entering text on behalf of the victim. This will likely be upgraded into an automatic transfer system in the future with the intent of speedily extracting money from its victims.
Finally, Medusa banker that has been around since 2020 has been spotted with various upgrades and has spread through botnets in Turkey, France, Spain and Italy among others. Disguised as 4K sports streaming apps, YouTube premium or even Avast Premium, the banker has extensive surveillance capabilities, including streaming the device screen, extracting contacts and SMS messages and keylogging on the victim’s device. The more recent version of this banker has been streamlined to require less permissions, likely with the intent of avoiding early discovery. Threat actors used a complex web of social media accounts and dynamically generated URLs to send commands to infected devices. There is indication that multiple threat actor groups have access to the same Medusa banker framework but use different techniques to spread the malware to victims. It is likely that we will see attempts at distributing this threat through droppers on official app stores in the future.
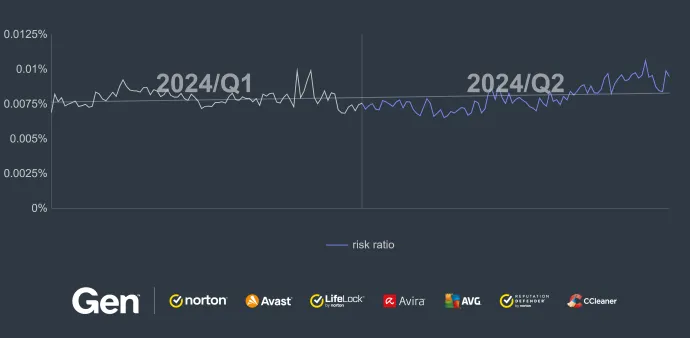
With the incoming new strains and evolutions of existing ones, we saw a gradual increase in protected users in Q2/2024. This comes with a higher risk ratio towards the end of the quarter. Strains like MoqHao mentioned in the last quarterly report are increasing their presence in the mobile threat ecosystem.
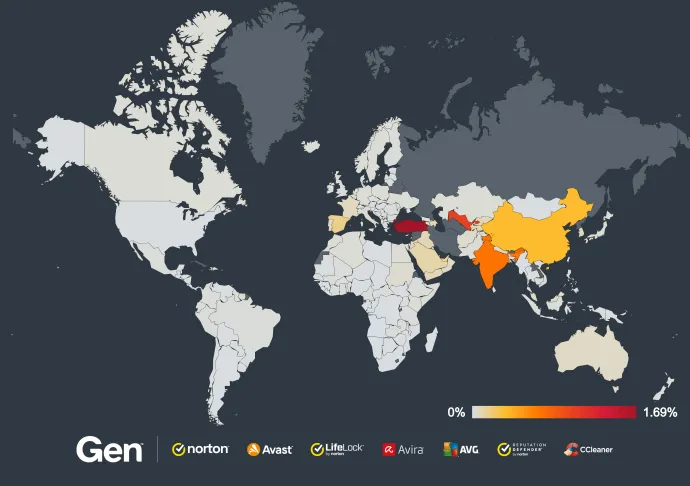
Turkey, India and Spain have highest risk ratio in Q2/2024, with India seeing over a 100% spike in protected users due to the risk of RewardSteal banker in recent months, likely pointing to a new campaign. We see a 47% increase in protected users in Japan due to the increased spread of MoqHao banker.
Spyware: Extensive Surveillance Continues
Spyware is used to spy on unsuspecting victims with the intent of extracting personal information such as messages, photos, location, or login details. It uses fake adverts, phishing messages, and modifications of popular applications to spread and harvest user information. State backed commercial spyware is becoming more prevalent and is used to target individuals with 0-day exploits.
New strains of spyware spring up in Q2/2024, targeting user data as well as actively spying on victims. XploitSpy is one such strain that snuck onto the PlayStore and extracted contact lists and files from infected devices. Conversely, AridSpy actively spied on its victims, taking a photo with the device camera in regular intervals and listening to surrounding audio. In our data, we see Spymax as the most prevalent spyware threat this quarter, with various altered versions being repackaged and served through phishing websites and third-party app stores. WhatsAppMods take second place, again focusing on victims' messages and using infected devices and accounts to further spread their malicious activity.
A long threat campaign seen running since November 2021 using XploitSpy has been targeting users in India and Pakistan, with fake messenger apps distributed through phishing websites and the PlayStore. Initially, the spyware was available on GitHub, but over time, threat actors added further obfuscation and improved their payload delivery methods. The spyware would pretend to connect to a fake C&C server if emulation was detected and it used a native library to hide its C&C server and functionality from static analysis. Once installed and active, it can extract contact lists and look for specific files on the device and extract these for the threat actors to utilize. The versions of XploitSpy that were present on the PlayStore had download numbers in the double digits, pointing to a more targeted campaign rather than the broad spread campaigns we have seen in other strains.
AridSpy has been seen targeting users in Egypt and Palestine with several campaigns using legitimate trojanized apps. Arid Viper APT group is likely behind the new spyware that is distributed through dedicated fake websites impersonating job seeker sites, messaging apps and a Palestinian Civil Registry app. AridSpy uses mutli-stage malicious payload delivery to avoid detection, it also features an anti-virus check that stops the payload delivery if it detects any security products on the victim’s device. Once the second payload is delivered and activated, threat actors will take photos with the device camera every hour and listen to surrounding audio. The spyware can also extract contact lists, SMS messages, WhatsApp and Facebook messenger conversations, photos and numerous other sensitive personal information from the victim’s device.
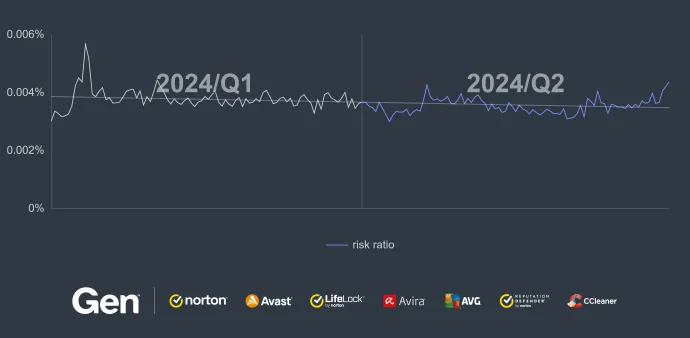
The risk ratio for Q2/2024 remained mostly consistent compared to last quarter. We saw a sharp rise in WhatsAppMod malwares which contributed to the increase prevalence of spyware this quarter. Conversely, there were not as many SpyLoan apps spotted on the PlayStore as last quarter.
Yemen continues to have the highest risk ratio of mobile spyware this quarter, followed by Turkey and Egypt. Brazil, United States and India had the highest numbers of protected users.
Jakub Vavra, Malware Analyst
